CVE-2022-26134 - Confluence RCE
This Playbook is part of the CVE-2022-26134 - Confluence RCE Pack.#
Supported versions
Supported Cortex XSOAR versions: 6.2.0 and later.
Atlassian has been made aware of the current active exploitation of a critical severity unauthenticated remote code execution vulnerability in Confluence Data Center and Server. The OGNL injection vulnerability allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance.
All versions of Confluence Server and Data Center prior to the fixed versions listed above are affected by this vulnerability.
Atlassian has released the following versions to address this issue:
Released versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4, and 7.18.1 which contain a fix for this issue.
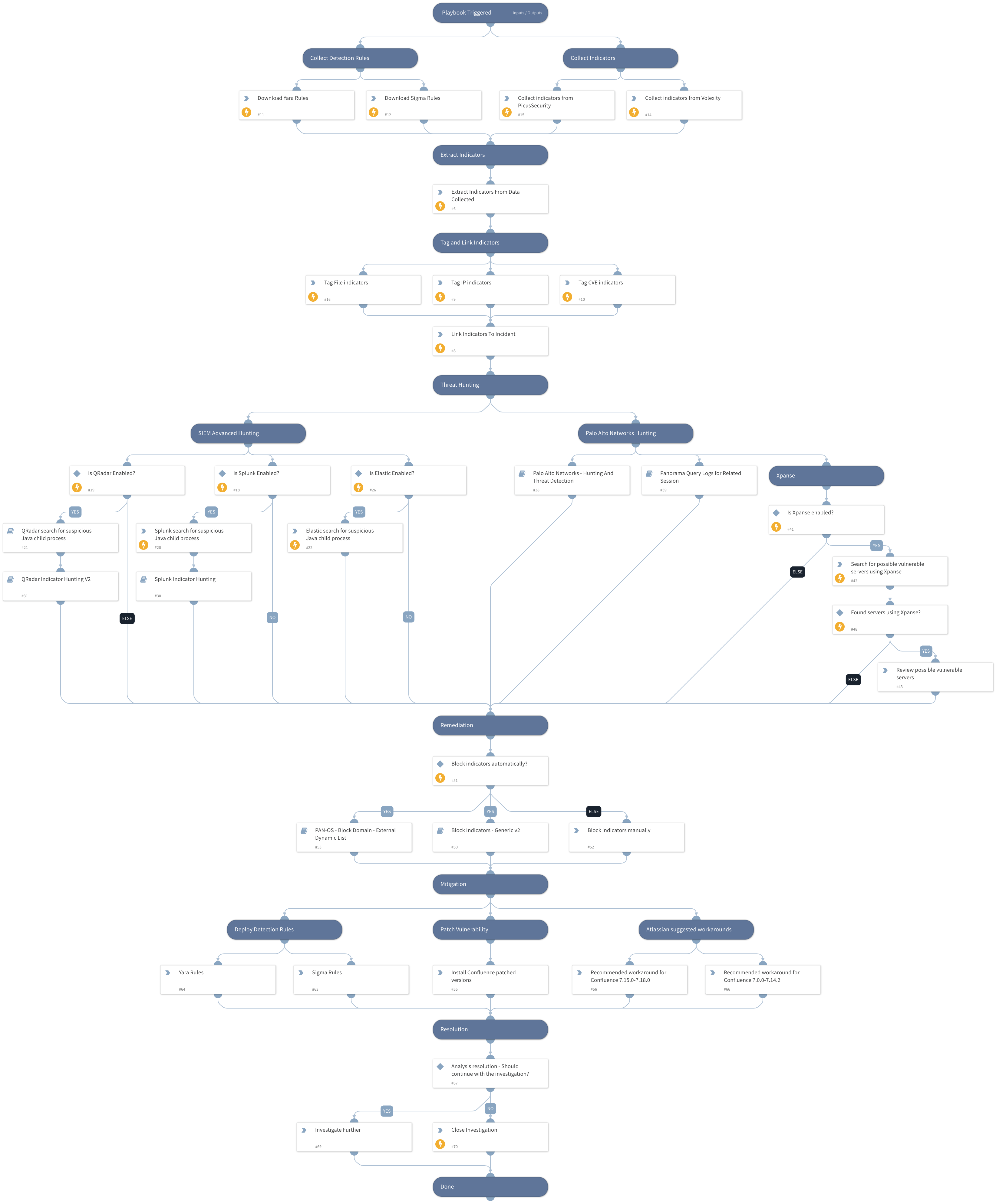
This playbook includes the following tasks:
- Collect detection rules.
- Exploitation patterns & IoCs hunting using PANW Next-Generation Firewalls and 3rd party SIEM products.
- Cortex Xpanse policies coverage.
- Provides Atlassian workarounds and patched versions.
More information:
Threat Brief: Atlassian Confluence Remote Code Execution Vulnerability (CVE-2022-26134) Confluence Security Advisory 2022-06-02
Note: This is a beta playbook, which lets you implement and test pre-release software. Since the playbook is beta, it might contain bugs. Updates to the pack during the beta phase might include non-backward compatible features. We appreciate your feedback on the quality and usability of the pack to help us identify issues, fix them, and continually improve.
Dependencies#
This playbook uses the following sub-playbooks, integrations, and scripts.
Sub-playbooks#
- PAN-OS - Block Domain - External Dynamic List
- Palo Alto Networks - Hunting And Threat Detection
- QRadar Indicator Hunting V2
- Block Indicators - Generic v2
- QRadar search for suspicious Java child process
- Panorama Query Logs
- Splunk Indicator Hunting
Integrations#
- Elasticsearch v2
Scripts#
- ParseHTMLIndicators
- IsIntegrationAvailable
- http
Commands#
- extractIndicators
- associateIndicatorsToIncident
- search
- expanse-get-issues
- closeInvestigation
- createNewIndicator
- splunk-search
Playbook Inputs#
| Name | Description | Default Value | Required |
|---|---|---|---|
| SplunkEarliestTime | Splunk search earliest time. | -7d@d | Optional |
| SplunkLatestTime | Splunk search latest time. | now | Optional |
| SplunkIndex | The Splunk index field to search in. Default is "*" | * | Optional |
| EDLDomainBlocklist | The EDL domain blocklist name. | Optional | |
| BlockIndicatorsAutomatically | Whether to block the indicators automatically or not. | True | Optional |
| QRadarTimeRange | The time range for QRadar query. | Last 7 DAYS | Optional |
| ElasticIndex | Elastic's index name in which to search. | Optional |
Playbook Outputs#
There are no outputs for this playbook.
Playbook Image#