redOverview
Use the Cisco Threat Grid integration to manage and query threat feeds and samples.
This integration was integrated and tested with Cisco Threat Grid v3.5.10.
Threat Grid Playbook
Use cases
Configure Threat Grid on Cortex XSOAR
-
Navigate to
Settings
>
Integrations
>
Servers & Services
.
-
Search for Threat Grid.
-
Click
Add instance
to create and configure a new integration instance.
You should configure the following settings:
-
Name
: a textual name for the integration instance.
-
Server URL (e.g.
https://192.168.0.1
)
-
API token
-
Trust any certificate (not secure)
-
Use system proxy settings
-
Click
Test
to validate the URLs, token, and connection.
Commands
You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook. After you successfully execute a command, a DBot message appears in the War Room with the command details.
-
Get samples: threat-grid-get-samples
-
Get a sample by sample ID: threat-grid-get-sample-by-id
-
Get the states of samples by sample ID: threat-grid-get-sample-state-by-id
-
Submit a sample for analysis: threat-grid-upload-sample
-
Search submissions: threat-grid-search-submissions
-
Get a sample analysis video by ID: threat-grid-get-video-by-id
-
Get a detailed overview of a sample: threat-grid-get-analysis-by-id
-
Get processes by ID: threat-grid-get-processes-by-id
-
Get a PCAP file for a sample by sample ID: threat-grid-get-pcap-by-id
-
Get warnings for a sample by sample ID: threat-grid-get-warnings-by-id
-
Get a summary analysis for a sample by sample ID: threat-grid-get-summary-by-id
-
Get a summary of threats detected during an analysis: threat-grid-get-threat-summary-by-id
-
Get the HTML report for a sample by sample ID: threat-grid-get-html-report-by-id
-
Download a sample as a ZIP file: threat-grid-download-sample-by-id
-
Get a list of IOCs found during a sample run: threat-grid-get-analysis-iocs
-
Get information for the logged in user: threat-grid-who-am-i
-
Get the rate limit for a specified user: threat-grid-user-get-rate-limit
-
Get a specific threat feed: threat-grid-get-specific-feed
-
Convert a URL to a file for detonation: threat-grid-url-to-file
-
Get rate limits for an organization: threat-grid-organization-get-rate-limit
-
Search IP addresses: threat-grid-search-ips
-
Get annotation data for an analysis: threat-grid-get-analysis-annotations
-
Search samples: threat-grid-search-samples
-
Search URLs: threat-grid-search-urls
-
Get the states of samples: threat-grid-get-samples-state
-
Get the threat feed for artifacts: threat-grid-feeds-artifacts
-
Get the threat feed for a domain: threat-grid-feeds-domain
-
Get the threat feed for an IP address: threat-grid-feeds-ip
-
Get the threat feed for a network stream: threat-grid-feeds-network-stream
-
Get the threat feed for a path: threat-grid-feeds-path
-
Get the threat feed for a URL: threat-grid-feeds-url
-
Get the artifacts for a sample ID by artifact ID: threat-grid-get-analysis-artifact
-
Get artifacts for a sample ID: threat-grid-get-analysis-artifacts
-
Get analysis data for an IOC: threat-grid-get-analysis-ioc
-
Get metadata for an analysis: threat-grid-get-analysis-metadata
-
Get data for a network stream: threat-grid-get-analysis-network-stream
-
Get the analysis for a threat stream: threat-grid-get-analysis-network-streams
-
Get data for a process ID in an analysis: threat-grid-get-analysis-process
-
Get data for an analysis process: threat-grid-get-analysis-processes
-
Submit URL for analysis: threat-grid-submit-urls
-
Run advanced search using the ThreatGrid search query: threat-grid-advanced-search
1. Get samples
Get samples on the Threat Grid platform. Input parameters are combined with
AND
statements. Only finished samples can be searched. Finished samples have a status of
succ
or
fail
.
Base Command
threat-grid-get-samples
Input
|
Argument Name
|
Description
|
Required
|
|
limit
|
Maximum number of results to return in the response
|
Optional
|
|
offset
|
The number of records to skip
|
Optional
|
|
sha256
|
SHA-256 of the submitted sample (only matches samples, not their artifacts)
|
Optional
|
|
md5
|
An MD5 checksum of the submitted sample (only matches samples, not their artifacts)
|
Optional
|
|
sha1
|
SHA-1 of the submitted sample, only matches samples, not their artifacts
|
Optional
|
|
id
|
ID of a sample
|
Optional
|
|
ids
|
Comma-separated list of sample IDs
|
Optional
|
|
ioc
|
IOC name
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before that time (YYYY-MM-DD Thhmmss+)
|
-hhmm e.g. : 2012-04-19T04:00:55-0500
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after that time (YYYY-MM-DD Thhmmss+)
|
-hhmm e.g. : 2012-04-19T04:00:55-0500"
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The sample ID
|
|
ThreatGrid.Sample.Filename
|
The sample filename
|
|
ThreatGrid.Sample.State
|
The sample state
|
|
ThreatGrid.Sample.Status
|
The sample status
|
|
ThreatGrid.Sample.MD5
|
The sample MD5
|
|
ThreatGrid.Sample.SHA1
|
The sample SHA-1
|
|
ThreatGrid.Sample.SHA256
|
The sample SHA-256
|
|
ThreatGrid.Sample.OS
|
The sample OS
|
|
ThreatGrid.Sample.SubmittedAt
|
The sample submission time
|
|
ThreatGrid.Sample.StartedAt
|
The sample analysis starting time
|
|
ThreatGrid.Sample.CompletedAt
|
The sample completion time
|
Command Example
!threat-grid-feeds-ip after=2018-01-18T00:00:00 before=2018-01-18T01:00:00 confidence=75 severity=75
Context Output
{
"ThreatGrid": {
"Sample": [
{
"Status": "job_done",
"SHA1": "f6ed96430b54a52740d3f7a0a246d1053ba7d779",
"CompletedAt": "2018-09-23T08:18:20Z",
"Filename": "8d3a3c399ac61a1e7ae6f6c68c67f1db2e88985066463a5ffb3dae0d552a64a5.exe",
"State": "succ",
"SubmittedAt": "2018-09-23T08:12:05Z",
"StartedAt": "2018-09-23T08:12:06Z",
"SHA256": "8d3a3c399ac61a1e7ae6f6c68c67f1db2e88985066463a5ffb3dae0d552a64a5",
"OS": "7601.18798.amd64fre.win7sp1_gdr.150316-1654",
"ID": "4bb1e6eed595513b2c07ba9bd4598f37",
"MD5": "c6bdbf3765854eef4981721947beba5f"
},
{
"Status": "job_done",
"SHA1": "6b7808dd69ff255e982f9940d067b356f030ff14",
"CompletedAt": "2018-09-23T08:18:28Z",
"Filename": "8a577adc1b387c0dfc445b4a6f9a5bb54de13018c960624c0dcf35145aa00b03.exe",
"State": "succ",
"SubmittedAt": "2018-09-23T08:12:07Z",
"StartedAt": "2018-09-23T08:12:08Z",
"SHA256": "8a577adc1b387c0dfc445b4a6f9a5bb54de13018c960624c0dcf35145aa00b03",
"OS": "7601.18798.amd64fre.win7sp1_gdr.150316-1654",
"ID": "b75b886bcd4b888c2c6a779736509b12",
"MD5": "eb6f2ad4dcba833fd4411301ed8ae40e"
}
]
}
}
Human Readable Output

2. Get a sample by sample ID
Get a Threat Grid sample by sample ID.
Base Command
threat-grid-get-sample-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The sample ID
|
|
ThreatGrid.Sample.Filename
|
The sample filename
|
|
ThreatGrid.Sample.State
|
The sample state
|
|
ThreatGrid.Sample.Status
|
The sample status
|
|
ThreatGrid.Sample.MD5
|
The sample MD5
|
|
ThreatGrid.Sample.SHA1
|
The sample SHA-1
|
|
ThreatGrid.Sample.SHA256
|
The sample SHA-256
|
|
ThreatGrid.Sample.OS
|
The sample OS
|
|
ThreatGrid.Sample.SubmittedAt
|
The sample submission time
|
|
ThreatGrid.Sample.StartedAt
|
The sample analysis starting time
|
|
ThreatGrid.Sample.CompletedAt
|
The sample completion time
|
Command Example
!threat-grid-get-sample-by-id id=052de338e02c4e013a4e9f5da8a87d5b
Context Example
{
"ThreatGrid": {
"Sample": {
"Status": "filetype_not_supported",
"SHA1": "a253ac433faa9ac59a9f73c540355bfe2f9fe708",
"CompletedAt": "2018-07-07T10:11:06Z",
"Filename": "WR Package(1).rar",
"State": "fail",
"SubmittedAt": "2018-07-07T10:11:04Z",
"StartedAt": "2018-07-07T10:11:05Z",
"SHA256": "9aa6f1189fa01f852e595d4c847a76613aa157d14addbdeb2ac011f443c811d7",
"OS": null,
"ID": "052de338e02c4e013a4e9f5da8a87d5b",
"MD5": "69e51e9f3a5ffbf6970a754ebda56edd"
}
}
}
Human Readable Output

3. Get the states of samples by sample ID
Get threat grid sample state by id
Base Command
threat-grid-get-sample-state-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Optional
|
|
ids
|
Comma-separated list of sample IDs
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The sample ID, globally unique, and the canonical identifier of this sample analysis
|
|
ThreatGrid.Sample.State
|
The state of the sample, one of a stable set of strings (“wait", "prep", "run", "proc", "succ", "fail”)
|
Command Example
!threat-grid-get-sample-state-by-id id=052de338e02c4e013a4e9f5da8a87d5b
Context Example
{
"ThreatGrid": {
"Sample": {
"State": "fail",
"ID": "052de338e02c4e013a4e9f5da8a87d5b"
}
}
}
Human Readable Output

4. Submit a sample for analysis
Submits a sample to Threat Grid for analysis.
Base Command
threat-grid-upload-sample
Input
|
Argument Name
|
Description
|
Required
|
|
file-id
|
The sample file. Click the chain icon after you upload a file in Cortex XSOAR to find the file-id.
|
Required
|
|
filename
|
The original file name of the sample (string)
|
Required
|
|
vm
|
A string identifying a specific VM to use. Options: win7-x64: Windows 7 64bit, win7-x64-2: Windows 7 64bit Profile 2, win7-x64-jp: Windows 7 64bit Japanese (Not available on Threat Grid appliances), win7-x64-kr: Windows 7 64bit Korean (Only available on Threat Grid appliances licensed for this VM), win10: Windows 10 (Not available on Threat Grid appliances). NOTE: The standard (English) VMs default to UTF-8 encoding. To support Korean and Japanese character sets, such as S-JIS, submit to the appropriate VM.
|
Optional
|
|
private
|
If specified and set to a value other than “false”, the sample will be marked private
|
Optional
|
|
tags
|
Comma-separated list of tags applied to this sample
|
Optional
|
|
playbook
|
Name of a playbook to apply to this sample run. none: Explicitly disables playbooks, default: Default Playbook, alt_tab_programs: Conduct Active Window Change, open_word_embedded_object: Open Embedded Object in Word Document, press_enter: Dialogue OK, visit_site: Visit Website Using Internet Explorer, close_file: Close Active Window, run_dialog_box_ie: Click Run on Internet Explorer Download Dialog Box, open_attachment_msg: Open Outlook Email Attachment, run_dialog_box_dde: Accept Microsoft Office Dialog Boxes to Open Dynamic Data Exchange Content. The current list of playbooks endpoints can be obtained by querying /api/v3/configuration/playbooks.
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The sample ID
|
|
ThreatGrid.Sample.Filename
|
The sample file name
|
|
ThreatGrid.Sample.State
|
The sample state
|
|
ThreatGrid.Sample.Status
|
The sample status
|
|
ThreatGrid.Sample.MD5
|
The sample MD5
|
|
ThreatGrid.Sample.SHA1
|
The sample SHA-1
|
|
ThreatGrid.Sample.SHA256
|
The sample SHA-256
|
|
ThreatGrid.Sample.OS
|
The sample OS
|
|
ThreatGrid.Sample.SubmittedAt
|
The sample submission time
|
Command Example
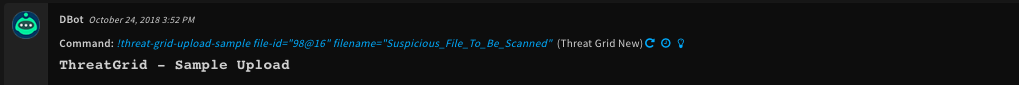
!threat-grid-upload-sample file-id=98@16 filename=Suspicious_File_To_Be_Scanned
Context Example
{
"ThreatGrid": {
"Sample": {
"Status": "pending",
"SHA1": "bd762a2d655e174fd935cc8a5e928bea738d666a",
"CompletedAt": null,
"Filename": "Suspicious_File_To_Be_Scanned",
"State": "wait",
"SubmittedAt": "2018-10-24T12:52:52Z",
"StartedAt": null,
"SHA256": "71a0ea5ebcc449feb2ab8954c239b89d9d629c77011b30f330bb61af091d2ad6",
"OS": "",
"ID": "ec7cb57929fdf3f313f3b1238ff042ca",
"MD5": "653e9905e882f44015e1023dcde66451"
}
},
"File": {
"Info": "image/jpeg",
"SHA1": "bd762a2d655e174fd935cc8a5e928bea738d666a",
"Name": "Image from iOS.jpg",
"Extension": "jpg",
"Size": 5405984,
"EntryID": "98@16",
"SSDeep": "98304:tSfriWHhyAU04siL8QOTgOZLG9CG6/2N76EUs0ELRd7xs6f2UXCpofGZ4oOBsU0:8W6B4siQtTR1GU/2No+fd2X/9J",
"SHA256": "71a0ea5ebcc449feb2ab8954c239b89d9d629c77011b30f330bb61af091d2ad6",
"Type": "JPEG image data, JFIF standard 1.01, aspect ratio, density 72x72, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=2, orientation=upper-left], baseline, precision 8, 4032x3024, frames 3\n",
"MD5": "653e9905e882f44015e1023dcde66451"
}
}
Human Readable Output
5. Search submissions
Search Threat Grid submissions.
Base Command
threat-grid-search-submissions
Input
|
Argument Name
|
Description
|
Required
|
|
q
|
Query text
|
Optional
|
|
user-only
|
Only display submissions created by the current user, as determined by the value of api_key
|
Optional
|
|
org-only
|
Only display submissions created by the current user's organization, as determined by the value of api_key.
|
Optional
|
|
term
|
Restrict matches to a subset of submission fields. The value of 'term' is a comma-delimited list of strings which select groups of fields
|
Optional
|
|
before
|
Return submissions created before specified time. Value is a time string, either ISO-8601, or free-form (see the
Chronic documentation
)
|
Optional
|
|
after
|
Return submissions created after specified time. Value is a time string, either ISO-8601, or free-form (see the
Chronic documentation
)
|
Optional
|
|
state
|
Restrict match to submissions in specific state or states. Value is a comma-delimited string containing one or more of the values ("wait", "proc", "succ", "fail")
|
Optional
|
|
advanced
|
Interpret 'q' as an advanced elasticsearch query, allowing matches by specific field, for example: https:// ... /search/submissions?q=sha256:1b4468 ... &advanced=true
|
Optional
|
|
sort_by
|
Sorts by "timestamp", "submitted_at", "analyzed_at", "filename", "type", "state", "threat" or "threat_score", or "login
|
Optional
|
|
sort_order
|
desc or asc
|
Optional
|
|
limit
|
Restrict the number of records returned
|
Optional
|
|
offset
|
Return matching submissions starting at the given offset
|
Optional
|
|
highlight
|
Provide a 'matches' field in results, indicating which fields were matched
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The sample ID
|
|
ThreatGrid.Sample.Filename
|
The name of the sample file
|
|
ThreatGrid.Sample.State
|
The state of the sample
|
|
ThreatGrid.Sample.Status
|
The status of the sample
|
|
ThreatGrid.Sample.MD5
|
The MD5 of the sample
|
|
ThreatGrid.Sample.SHA1
|
The SHA-1 of the sample
|
|
ThreatGrid.Sample.SHA256
|
The SHA-256 of the sample
|
|
ThreatGrid.Sample.SubmittedAt
|
Time of submission for the sample
|
|
ThreatGrid.Sample.ThreatScore
|
The threat score of the sample
|
Command Example
!threat-grid-search-submissions limit=2
Context Example
{
"ThreatGrid": {
"Sample": [
{
"Status": "job_done",
"SHA1": "e823f52975e7b2dff0c5873973682dd5c2eb2464",
"CompletedAt": null,
"ThreatScore": 64,
"Filename": "url_as_file",
"State": "succ",
"SubmittedAt": "2018-07-04T10:25:53Z",
"StartedAt": null,
"SHA256": "da6de9ab720e1c763290fdad040113881e7d7443780283ff71970d3e160aa374",
"OS": null,
"ID": "47a9ca675ba509457bfd8cbe2a5b2189",
"MD5": "08db479ddee306addef0946194374795"
},
{
"Status": "job_done",
"SHA1": "e823f52975e7b2dff0c5873973682dd5c2eb2464",
"CompletedAt": null,
"ThreatScore": 64,
"Filename": "url_as_file",
"State": "succ",
"SubmittedAt": "2018-07-03T20:29:04Z",
"StartedAt": null,
"SHA256": "da6de9ab720e1c763290fdad040113881e7d7443780283ff71970d3e160aa374",
"OS": null,
"ID": "18bbd9bd6bf3be6a2f842b72cc19668f",
"MD5": "08db479ddee306addef0946194374795"
}
]
}
}
Human Readable Output

6. Get a sample analysis video by ID
Get the sample analysis video by ID.
Base Command
threat-grid-get-video-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.Id
|
string
|
The sample ID
|
Command Example
!threat-grid-get-video-by-id id=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"Sample": {
"Id": "9798717402a40970a2d043014d9a6170"
}
},
"File": {
"Info": "video/webm",
"SHA1": "28d2b83753b713e3fb40d896ca3cbff13735f8c0",
"Name": "9798717402a40970a2d043014d9a6170.webm",
"Extension": "webm",
"Size": 1038907,
"EntryID": "117@16",
"SSDeep": "24576:u5/QP+OM+62I73Hi6RQ7MM4uyeL+I2zcvu3AYApDl29d9xG:u/IM+6v3HpM4rI2L3jACLG",
"SHA256": "ce7c155cde9d2d637a8f0e48c5e9d183a7c9756bc02d6ee505bfcda19f01573e",
"Type": ", created: Thu Jul 11 00:22:26 1974, modified: Sun Jul 17 00:26:42 2033\n",
"MD5": "7aeb2b515af0c5e1c8cfca234377e44f"
}
}
Human Readable Output

7. Get a detailed overview of a sample
The detailed overview of dynamic and static analysis results for the sample.
Base Command
threat-grid-get-analysis-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
|
limit
|
Limits the results, default is 20. To return all results, set the value to "".
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The ID of the sample for which the report was downloaded
|
|
Demisto.File
|
File containing unfiltered result
|
|
ThreatGrid.Sample.VM.ID
|
The VM ID for the sample
|
|
ThreatGrid.Sample.VM.Name
|
The VM Name for the sample
|
|
ThreatGrid.Sample.StartedAt
|
Start time of the analysis
|
|
ThreatGrid.Sample.Runtime
|
Runtime of the analysis
|
|
ThreatGrid.Sample.FileName
|
File name of the sample
|
|
ThreatGrid.Sample.Size
|
Size of the sample
|
|
ThreatGrid.Sample.MD5
|
The sample MD5 value
|
|
ThreatGrid.Sample.SHA1
|
The sample's SHA-1 value
|
|
ThreatGrid.Sample.SHA256
|
The sample's SHA-256 value
|
|
ThreatGrid.Sample.MagicType
|
Sample magic type
|
|
ThreatGrid.Sample.Type
|
Sample's file type
|
|
ThreatGrid.Sample.ThreatScore
|
The threat score of the sample
|
|
ThreatGrid.Sample.HeuristicScore
|
The sample's heuristic score
|
|
ThreatGrid.Sample.FilesDeleted
|
The files that were created during the analysis
|
|
ThreatGrid.Sample.FileCreated
|
The files that were created during the analysis
|
|
ThreatGrid.Sample.FilesModified
|
The files that were modified during the analysis
|
|
ThreatGrid.Sample.Directory
|
The directory of the sample
|
|
ThreatGrid.Sample.CMD
|
The command line execution of the sample
|
|
ThreatGrid.Sample.ProcessName
|
The process name of the sample
|
|
ThreatGrid.Sample.Destination
|
The destination IP of the sample
|
|
ThreatGrid.Sample.DestinationPort
|
The destination port of the sample
|
|
ThreatGrid.Sample.PacketSize
|
Packet size in bytes
|
|
ThreatGrid.Sample.VT.Hits
|
Sample malicious hits in VirusTotal
|
|
ThreatGrid.Sample.VT.Engines
|
Number of engines that scanned the Sample on VirusTotal
|
|
ThreatGrid.Artifact.Yara
|
Artifact ID (yara signature name
|
|
ThreatGrid.Artifact.Tags
|
Artifact tags
|
|
ThreatGrid.Artifact.FamilyName
|
Artifact family name
|
|
ThreatGrid.Artifact.ThreatName
|
Artifact threat name
|
Command Example
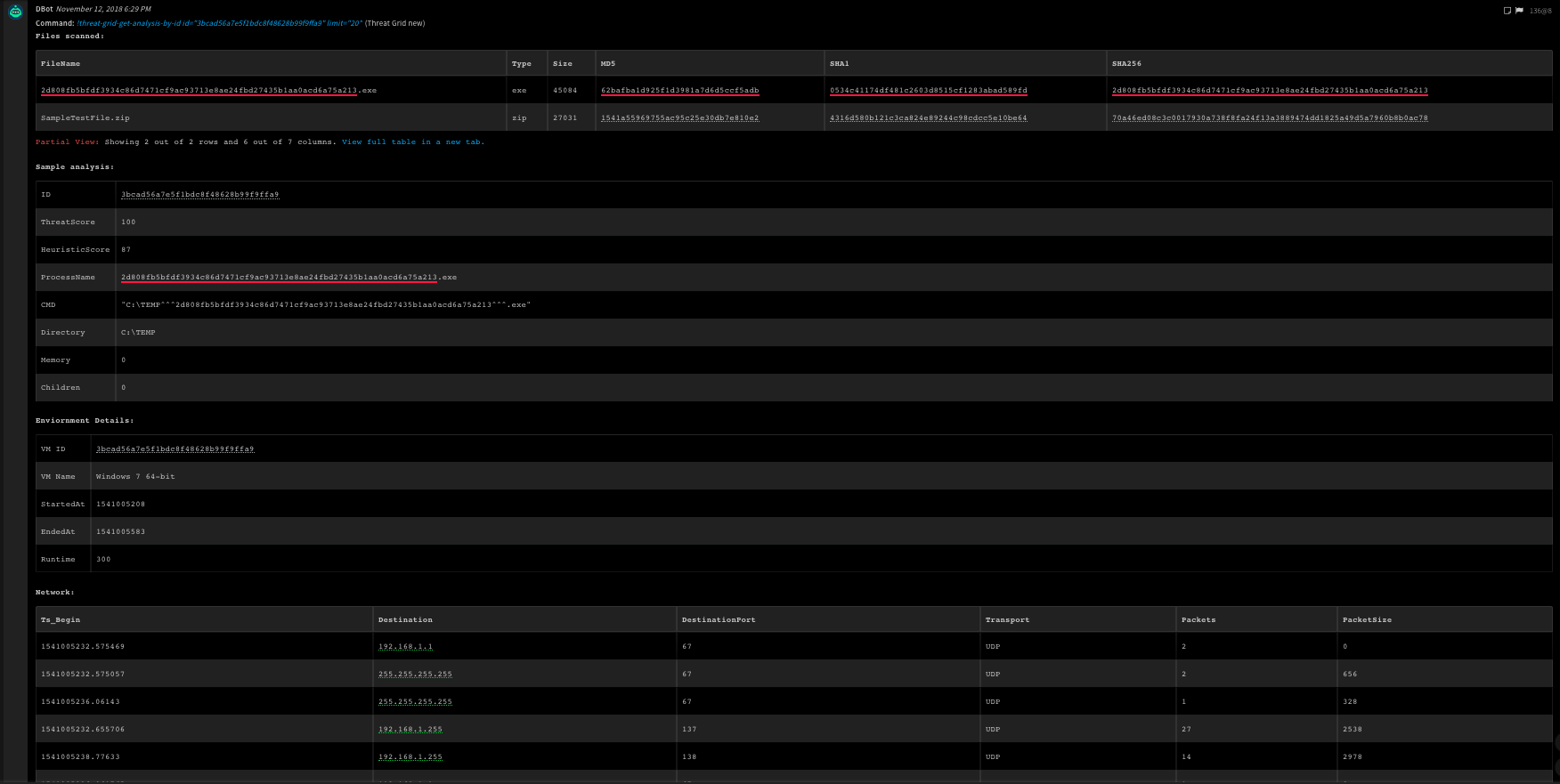
!threat-grid-get-analysis-by-id id=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"Sample": {
"Id": "9798717402a40970a2d043014d9a6170"
}
},
"InfoFile": {
"Info": "application/json",
"Name": "9798717402a40970a2d043014d9a6170-analysis.json",
"Extension": "json",
"EntryID": "124@16",
"Type": "ASCII text, with very long lines\n",
"Size": 132549
}
Human Readable Output
8. Get processes by ID
Returns a JSON object that contains a timeline of all process activities as determined by the dynamic analysis engine.
Base Command
threat-grid-get-processes-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.Id
|
string
|
The ID of the sample that the PCAP needs to be downloaded for.
|
Command Example
!threat-grid-get-processes-by-id id=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"Sample": {
"Id": "9798717402a40970a2d043014d9a6170"
}
},
"File": {
"Info": "application/json",
"SHA1": "365d2e8f7d25c24040a0ea92ae2f14a49cb3a683",
"Name": "9798717402a40970a2d043014d9a6170-processes.json",
"Extension": "json",
"Size": 526700,
"EntryID": "131@16",
"SSDeep": "1536:RWK0+6BL3y3bdvHruY3kvaRLERpXS2wsxWsw9I1O8PDHK1YR50l1n:RWK0+6BL3y3bdvHruY3kvaRLERpXS2w/",
"SHA256": "12f9c229f0eaa2629871db1f7f61e67fa8604ec5a6674378e14c7168f6b95201",
"Type": "ASCII text, with very long lines\n",
"MD5": "b586252a2a6b1681d07667a8c64daa70"
}
}
Human Readable Output

9. Get a PCAP file for a sample by sample ID
Get the tcpdump PCAP file for a specific sample ID, with all the network activity of the sample.
Base Command
threat-grid-get-pcap-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.Id
|
string
|
The ID of the sample that the PCAP needs to be downloaded for.
|
Command Example
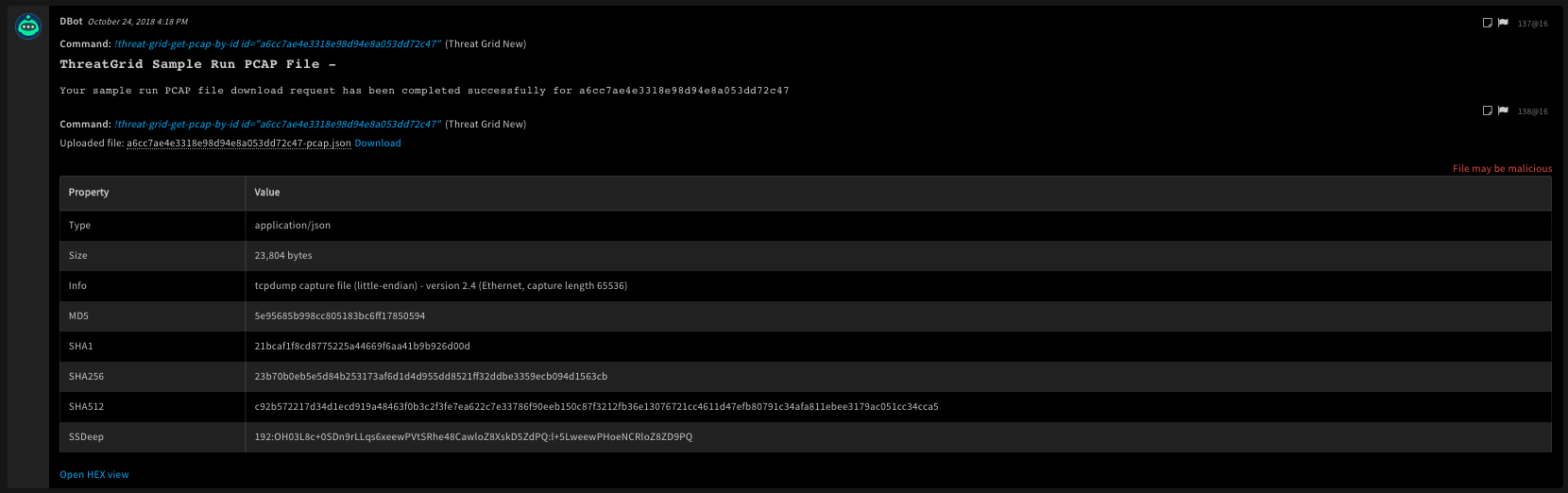
!threat-grid-get-pcap-by-id id=a6cc7ae4e3318e98d94e8a053dd72c47
Context Example
{
"ThreatGrid": {
"Sample": {
"Id": "a6cc7ae4e3318e98d94e8a053dd72c47"
}
},
"File": {
"Info": "application/json",
"SHA1": "21bcaf1f8cd8775225a44669f6aa41b9b926d00d",
"Name": "a6cc7ae4e3318e98d94e8a053dd72c47-pcap.json",
"Extension": "json",
"Size": 23804,
"EntryID": "138@16",
"SSDeep": "192:OH03L8c+0SDn9rLLqs6xeewPVtSRhe48CawloZ8XskD5ZdPQ:l+5LweewPHoeNCRloZ8ZD9PQ",
"SHA256": "23b70b0eb5e5d84b253173af6d1d4d955dd8521ff32ddbe3359ecb094d1563cb",
"Type": "tcpdump capture file (little-endian) - version 2.4 (Ethernet, capture length 65536)\n",
"MD5": "5e95685b998cc805183bc6ff17850594"
}
}
Human Readable Output
10. Get warnings for a sample by sample ID
Returns a JSON structure that describes warnings that occurred during the analysis.
Base Command
threat-grid-get-warnings-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.Id
|
string
|
The sample ID
|
Command Example
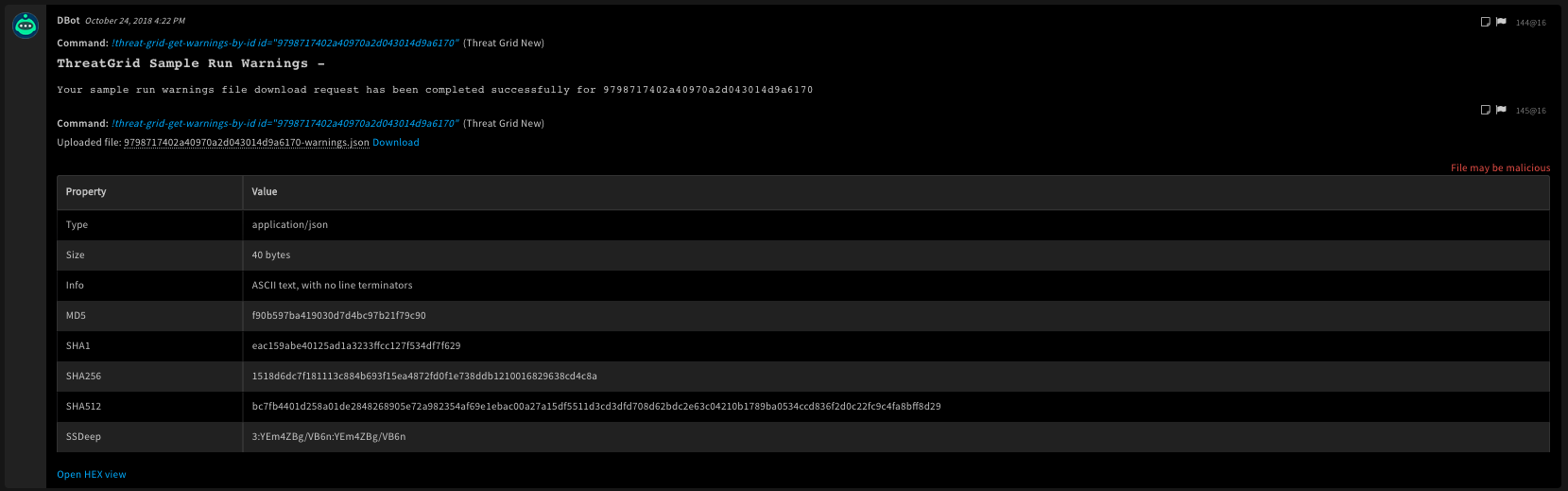
!threat-grid-get-warnings-by-id id=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"Sample": {
"Id": "9798717402a40970a2d043014d9a6170"
}
},
"File": {
"Info": "application/json",
"SHA1": "eac159abe40125ad1a3233ffcc127f534df7f629",
"Name": "9798717402a40970a2d043014d9a6170-warnings.json",
"Extension": "json",
"Size": 40,
"EntryID": "145@16",
"SSDeep": "3:YEm4ZBg/VB6n:YEm4ZBg/VB6n",
"SHA256": "1518d6dc7f181113c884b693f15ea4872fd0f1e738ddb1210016829638cd4c8a",
"Type": "ASCII text, with no line terminators\n",
"MD5": "f90b597ba419030d7d4bc97b21f79c90"
}
}
Human Readable Output
11. Get a summary analysis for a sample by sample ID
Returns summary analysis information.
Base Command
threat-grid-get-summary-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.ID
|
string
|
The sample ID
|
|
ThreatGrid.Sample.AnalysisSummary.RegistryCount
|
number
|
The registry count of the sample
|
|
ThreatGrid.Sample.AnalysisSummary.FileName
|
string
|
The filename of the sample
|
|
ThreatGrid.Sample.AnalysisSummary.SHA256
|
string
|
The SHA-256 hash of the sample
|
|
ThreatGrid.Sample.AnalysisSummary.SampleType
|
string
|
The sample type
|
|
ThreatGrid.Sample.AnalysisSummary.FirstSeen
|
date
|
The timestamp when the sample was first seen
|
|
ThreatGrid.Sample.AnalysisSummary.LastSeen
|
date
|
The timestamp when the sample was last seen
|
Command Example
!threat-grid-get-summary-by-id id=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"Sample": {
"ArtifactsCount": {
"Extracted": 1,
"Disk": 3,
"Network": null,
"Memory": 1
},
"AnalysisSummary": {
"RegistryCount": 9,
"SampleType": "9798717402a40970a2d043014d9a6170",
"FileName": "Suspicious_File_To_Be_Scanned.pdf",
"LastSeen": "2018-08-08T10:59:45Z",
"SHA256": "ad5902780a08a34af6d6b1a654fdc6a66d08bf8e7bdaf0d5fc0d0b2ca250144f",
"FirstSeen": "2018-08-08T10:59:45Z"
},
"ID": "9798717402a40970a2d043014d9a6170"
}
}
}
Human Readable Output
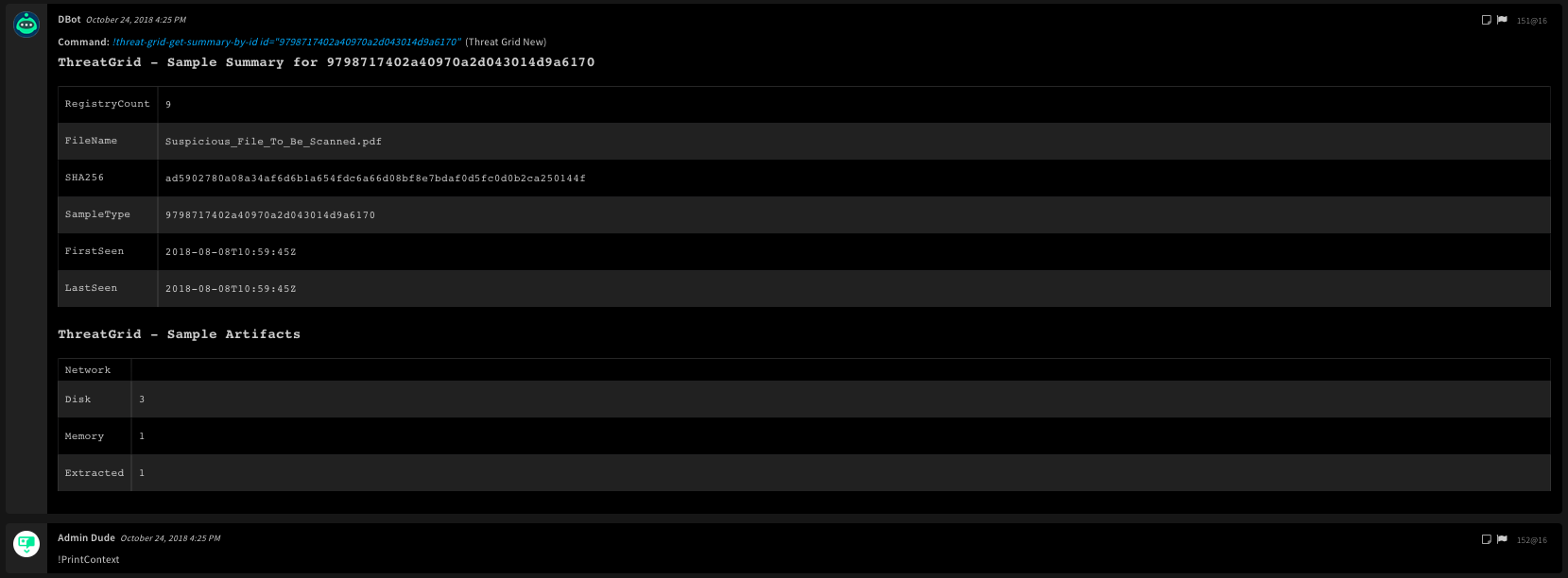
12. Get a summary of threats detected during an analysis
Returns a summary of the threats detected during analysis
Base Command
threat-grid-get-threat-summary-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.ID
|
string
|
The sample ID
|
|
ThreatGrid.Sample.MaxSeverity
|
number
|
The sample maximum severity
|
|
ThreatGrid.Sample.Score
|
number
|
The sample score
|
|
ThreatGrid.Sample.Count
|
number
|
The sample count
|
|
ThreatGrid.Sample.MaxConfidence
|
number
|
The sample maximum confidence
|
|
DBotScore.Indicator
|
string
|
The indicator value
|
|
DBotScore.Score
|
number
|
The indicator's score
|
|
DBotScore.Vendor
|
string
|
The indicator's vendor
|
|
DBotScore.Type
|
string
|
The indicator's type
|
|
ThreatGrid.Sample.ThreatFeeds
|
unknown
|
The sample threat feeds
|
Command Example
!threat-grid-get-threat-summary-by-id id=58e5e66b31484a8529b80a18a33e0814
Context Example
{
"DBotScore": {
"Vendor": "ThreatGrid",
"Indicator": "58e5e66b31484a8529b80a18a33e0814",
"Score": 1,
"Type": "Sample ID"
},
"ThreatGrid": {
"Sample": {
"Count": 0,
"ThreatFeeds": [],
"MaxSeverity": 0,
"Score": 0,
"MaxConfidence": 0,
"ID": "58e5e66b31484a8529b80a18a33e0814"
}
}
}
Human Readable Output
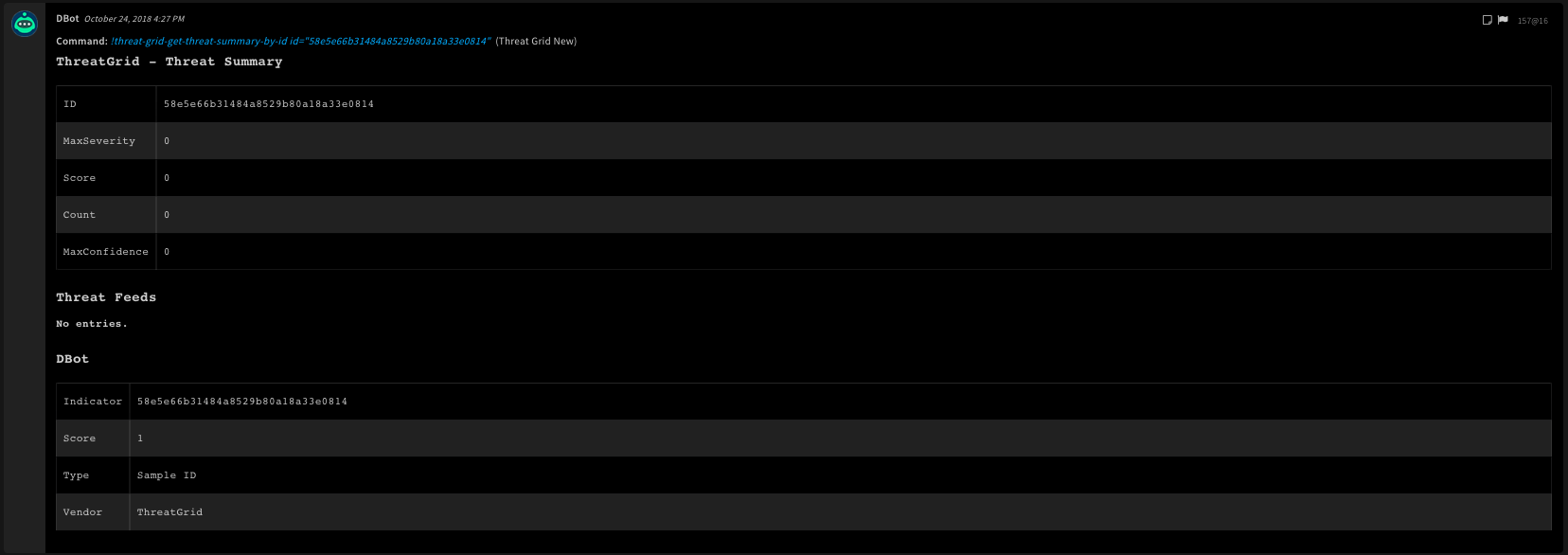
13. Get the HTML report for a sample by sample ID
Get the
report.html
file for a specific sample ID. This is a stand-alone file with a complete report on the sample run. It is designed to be emailed or printed.
Base Command
threat-grid-get-html-report-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.Sample.Id
|
string
|
The ID of the sample that the report was downloaded for
|
Command Example
!threat-grid-get-html-report-by-id id=6712d1b712dda4aa63d6073477c367c4
Context Example
{
"ThreatGrid": {
"Sample": {
"Id": "6712d1b712dda4aa63d6073477c367c4"
}
},
"InfoFile": {
"Info": "text/html; charset=utf-8",
"Name": "6712d1b712dda4aa63d6073477c367c4-report.html",
"Extension": "html",
"EntryID": "175@16",
"Type": "HTML document text, UTF-8 Unicode text, with very long lines, with CRLF line terminators\n",
"Size": 771771
}
}
Human Readable Output

14. Download a sample as a ZIP file
Download a sample by using its ID. The downloaded file is an archive of the sample itself, in a zip format as a form of quarantine.
Base Command
threat-grid-download-sample-by-id
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The ID of the sample to download
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.DownloadedSamples.Id
|
string
|
The ID of the downloaded sample
|
Command Example
!threat-grid-download-sample-by-id id=6712d1b712dda4aa63d6073477c367c4
Context Example
{
"ThreatGrid": {
"DownloadedSamples": {
"Id": "6712d1b712dda4aa63d6073477c367c4"
}
},
"File": {
"Info": "application/zip",
"SHA1": "804ac7075ec66262cb267ad56acdff2f507e28a7",
"Name": "6712d1b712dda4aa63d6073477c367c4-sample.zip",
"Extension": "zip",
"Size": 6972,
"EntryID": "184@16",
"SSDeep": "192:R56It4RdYQq8ViAAybtWGIEOV2H6ryqvA7SI0p:/6IKRdYXnyboVMuAk",
"SHA256": "97ae6411493dea29497d94db876af85958d23cdccff574b86be96ad15a4a004a",
"Type": "Zip archive data, at least v2.0 to extract\n",
"MD5": "6dec1a3d1e4df557c2dba87c16f75542"
}
}
Human Readable Output

15. Get a list of IOCs found during a sample run
Returns a JSON list of the Indicators of Compromise identified in this sample run.
Base Command
threat-grid-get-analysis-iocs
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
|
ioc
|
The IOC name you want to fetch details for
|
Optional
|
|
limit
|
Limit the number of indicators you would like to see. The list is sorted by indicator severity in descending order.
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.IOCs.Title
|
The title of the IOC
|
|
ThreatGrid.IOCs.Confidence
|
The confidence of the IOC
|
|
ThreatGrid.IOCs.Severity
|
The severity of the IOC
|
|
ThreatGrid.IOCs.IOC
|
The Threat Grid IOC
|
|
ThreatGrid.IOCs.IOCCategory
|
The IOC category of the IOC
|
|
DBotScore.Indicator
|
The indicator value
|
|
DBotScore.Vendor
|
The indicator vendor
|
|
DBotScore.Type
|
The indicator type
|
|
DBotScore.Score
|
The indicator score
|
|
ThreatGrid.IOCs.Data.IP
|
The IP of the IOC
|
|
ThreatGrid.IOCs.Data.URL
|
The URL of the IOC
|
|
ThreatGrid.IOCs.Data.Domain
|
The domain of the IOC
|
|
ThreatGrid.IOCs.Data.Path
|
The path of the IOC
|
|
ThreatGrid.IOCs.Data.SHA256
|
SHA-256 value of the IOC
|
|
ThreatGrid.IOCs.Tags
|
IOC tags
|
Command Example
!threat-grid-get-analysis-iocs id=a6cc7ae4e3318e98d94e8a053dd72c47
Context Example
{
"DBotScore": [
{
"Vendor": "ThreatGrid",
"Indicator": "antivirus-flagged-artifact",
"Score": 2,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "pe-uses-dot-net",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "dns-dynamic-domain",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "memory-execute-readwrite",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "modified-executable",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "netsh-firewall-generic",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "network-snort-malware",
"Score": 3,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "registry-autorun-key-data-dir",
"Score": 2,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "firewall-exception-user-dir",
"Score": 3,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "modified-file-in-user-dir",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "netsh-firewall-add",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "registry-autorun-key-modified",
"Score": 2,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "malware-known-trojan-av",
"Score": 3,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "feed-domain-rat",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "network-fast-flux-domain",
"Score": 1,
"Type": "IOC"
},
{
"Vendor": "ThreatGrid",
"Indicator": "artifact-flagged-anomaly",
"Score": 1,
"Type": "IOC"
}
],
"ThreatGrid": {
"IOCs": [
{
"Confidence": 80,
"Severity": 80,
"Tags": [
"file"
],
"IOCCategory": [
"forensics"
],
"Title": "Artifact Flagged by Antivirus",
"Data.Path": [
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe"
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "antivirus-flagged-artifact"
},
{
"Confidence": 60,
"Severity": 35,
"Tags": [
"artifact",
"library",
"PE"
],
"IOCCategory": [
"attribute"
],
"Title": "Executable Artifact Uses .NET",
"Data.Path": [
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe"
],
"Data.URL": [
null,
null,
null
],
"Data.SHA256": [
null,
null,
null
],
"IOC": "pe-uses-dot-net"
},
{
"Confidence": 60,
"Severity": 50,
"Tags": [
"evasion"
],
"IOCCategory": [
"network"
],
"Title": "Dynamic DNS Domain Detected",
"Data.Path": [
null,
null
],
"Data.URL": [
null,
null
],
"Data.SHA256": [
null,
null
],
"IOC": "dns-dynamic-domain"
},
{
"Confidence": 50,
"Severity": 50,
"Tags": [
"memory"
],
"IOCCategory": [
"evasion"
],
"Title": "Potential Code Injection Detected",
"Data.Path": [
null
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "memory-execute-readwrite"
},
{
"Confidence": 100,
"Severity": 60,
"Tags": [
"executable",
"file",
"process",
"PE"
],
"IOCCategory": [
"file",
"persistence"
],
"Title": "Process Modified an Executable File",
"Data.Path": [
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe"
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "modified-executable"
},
{
"Confidence": 100,
"Severity": 70,
"Tags": [
"process",
"firewall",
"bypass",
"networking"
],
"IOCCategory": [
"weakening"
],
"Title": "Netsh.exe Used to Alter Windows Firewall",
"Data.Path": [
null
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "netsh-firewall-generic"
},
{
"Confidence": 95,
"Severity": 95,
"Tags": [
"snort",
"malware"
],
"IOCCategory": [
"network"
],
"Title": "Network Stream Marked as Malware by Snort",
"Data.Path": [
null
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "network-snort-malware"
},
{
"Confidence": 100,
"Severity": 90,
"Tags": [
"process",
"autorun",
"registry",
"compound"
],
"IOCCategory": [
"persistence"
],
"Title": "Registry Persistence Mechanism Refers to an Executable in a User Data Directory",
"Data.Path": [
null,
null
],
"Data.URL": [
null,
null
],
"Data.SHA256": [
null,
null
],
"IOC": "registry-autorun-key-data-dir"
},
{
"Confidence": 95,
"Severity": 100,
"Tags": [
"file",
"trojan",
"artifact",
"compound"
],
"IOCCategory": [
"weakening"
],
"Title": "User Directory FireWall Exception",
"Data.Path": [
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe"
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "firewall-exception-user-dir"
},
{
"Confidence": 80,
"Severity": 70,
"Tags": [
"executable",
"file",
"process"
],
"IOCCategory": [
"file"
],
"Title": "Process Modified File in a User Directory",
"Data.Path": [
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe"
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "modified-file-in-user-dir"
},
{
"Confidence": 100,
"Severity": 70,
"Tags": [
"process",
"firewall",
"bypass",
"networking"
],
"IOCCategory": [
"weakening"
],
"Title": "Netsh.exe Used to Add Program to Firewall Allowed Program List",
"Data.Path": [
null
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "netsh-firewall-add"
},
{
"Confidence": 60,
"Severity": 80,
"Tags": [
"process",
"autorun",
"registry"
],
"IOCCategory": [
"persistence"
],
"Title": "Process Modified Autorun Registry Key Value",
"Data.Path": [
null,
null,
null
],
"Data.URL": [
null,
null,
null
],
"Data.SHA256": [
null,
null,
null
],
"IOC": "registry-autorun-key-modified"
},
{
"Confidence": 95,
"Severity": 100,
"Tags": [
"trojan",
"RAT"
],
"IOCCategory": [
"malware"
],
"Title": "Artifact Flagged as Known Trojan by Antivirus",
"Data.Path": [
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe"
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "malware-known-trojan-av"
},
{
"Confidence": 25,
"Severity": 25,
"Tags": [
"communications",
"command and control"
],
"IOCCategory": [
"network"
],
"Title": "RAT Queried Domain",
"Data.Path": [
null
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "feed-domain-rat"
},
{
"Confidence": 20,
"Severity": 35,
"Tags": [
"network",
"ttl",
"dns",
"fast flux",
"command and control"
],
"IOCCategory": [
"network"
],
"Title": "DNS Response Contains Low Time to Live (TTL) Value",
"Data.Path": [
null
],
"Data.URL": [
null
],
"Data.SHA256": [
null
],
"IOC": "network-fast-flux-domain"
},
{
"Confidence": 80,
"Severity": 60,
"Tags": [
"anomaly",
"static"
],
"IOCCategory": [
"forensics"
],
"Title": "Static Analysis Flagged Artifact As Anomalous",
"Data.Path": [
"\\TEMP\\2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe",
"\\Users\\Administrator\\AppData\\Roaming\\Mmas.exe",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d.exe"
],
"Data.URL": [
null,
null,
null
],
"Data.SHA256": [
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d",
"2c0146af31a67ef3f8193761d710751641e67690df2599990e44af201dd71a1d"
],
"IOC": "artifact-flagged-anomaly"
}
]
}
}
Human Readable Output
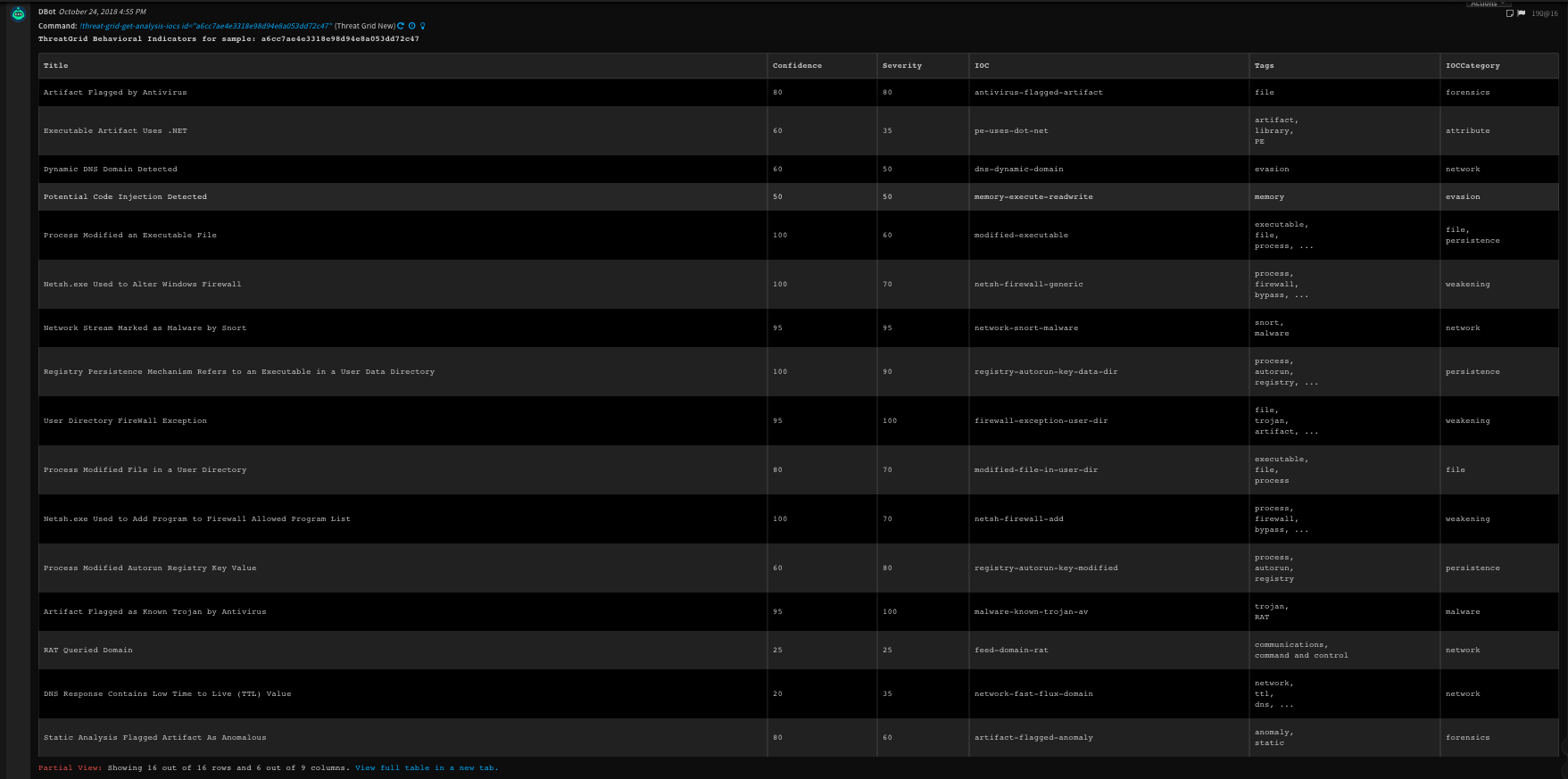
16. Get information for the logged in user
Return information for the logged in user.
Base Command
threat-grid-who-am-i
Input
There is no input for this command.
Context Output
|
Path
|
Description
|
|
ThreatGrid.User.Email
|
Email of the logged in user
|
|
ThreatGrid.User.Login
|
Login ID of the logged in user
|
|
ThreatGrid.User.Name
|
Name of the logged in user
|
|
ThreatGrid.User.OrganizationId
|
The Organization ID of the logged in user
|
|
ThreatGrid.User.Role
|
Role of the logged in user
|
Command Example
!threat-grid-who-am-i
Context Example
{
"ThreatGrid": {
"User": {
"Organization": 42,
"Login": "String",
"Role": "org-admin",
"Email": "String",
"Name": "String"
}
}
}
Human Readable Output

17. Get the rate limit for a specified user
Get rate limit for a specific user name. ThreatGrid employs a simple rate limiting method for sample submissions by specifying the number of samples which can be submitted within some variable time period by a user. Multiple rate limits can be employed to form overlapping submission limits. For example, 20 submissions per hour AND 400 per day.
Base Command
threat-grid-user-get-rate-limit
Input
|
Argument Name
|
Description
|
Required
|
|
login
|
User login name
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.User.RateLimit.Minutes
|
number
|
Array of array(s) representing submission(s) per minute(s) or the string"nil" to clear the value. Example: [[5, 1440]] which represents 5 samples per day. This field represent the minutes.
|
|
ThreatGrid.User.RateLimit.Samples
|
number
|
Array of array(s) representing submission(s) per minute(s) or the string"nil" to clear the value. Example: [[5, 1440]] which represents 5 samples per day. This field represent the number of samples allowed.
|
|
ThreatGrid.User.RateLimit.SubmissionWaitSeconds
|
number
|
The number of seconds to wait for a submission to get uploaded on the platform.
|
|
ThreatGrid.User.RateLimit.SubmissionsAvailable
|
number
|
The number of submissions available for the specified username
|
Command Example
!threat-grid-user-get-rate-limit login="user_name"
Context Example
{
"ThreatGrid": {
"User": {
"RateLimit": [
{
"SubmissionWaitSeconds": 0,
"SubmissionsAvailable": null
}
]
}
}
}
Human Readable Output
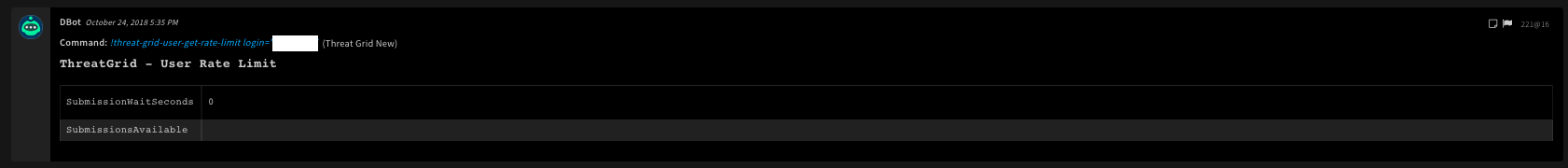
18. Get a specific threat feed
Gets a specific threat feed.
Base Command
threat-grid-get-specific-feed
Input
|
Argument Name
|
Description
|
Required
|
|
feed-name
|
The feed name
|
Required
|
|
feed-period
|
Feed daily date (YYYY-MM-DD)
|
Optional
|
|
output-type
|
The output type
|
Optional
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-get-specific-feed feed-name=rat-dns output-type=csv
Human Readable Output
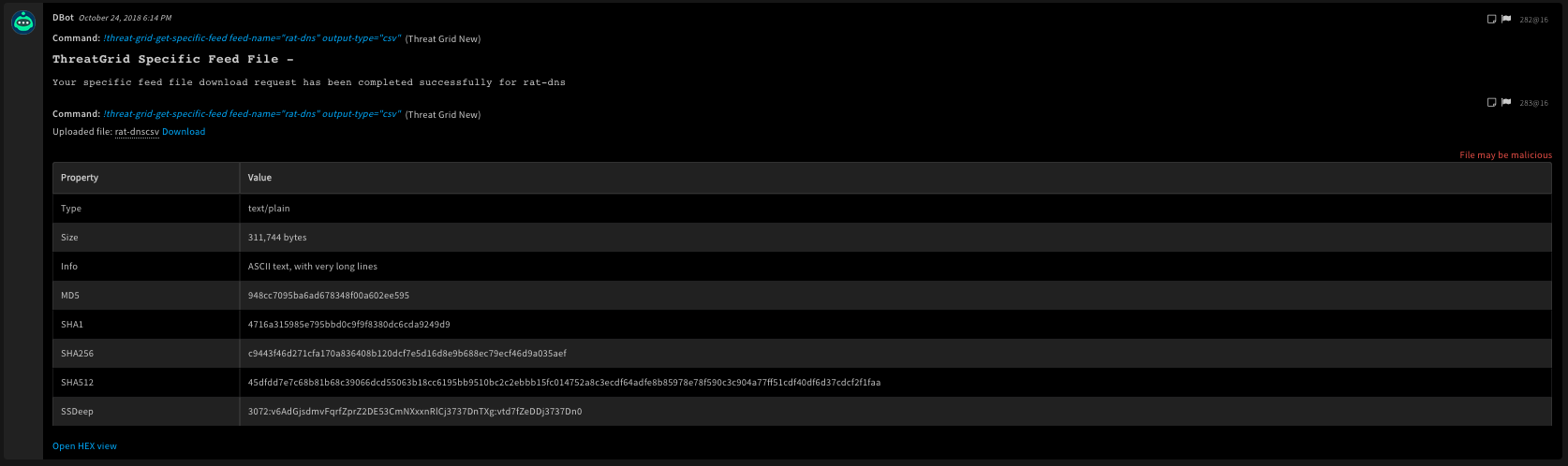
19. Convert a URL to a file for detonation
Convert a URL into a file for Threat Grid file detonation.
Base Command
threat-grid-url-to-file
Input
|
Argument Name
|
Description
|
Required
|
|
urls
|
Comma-separated list of URLs to convert
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-url-to-file urls=www.google.com
Human Readable Output

20. Get rate limits for an organization
Get rate limits applied to an organization. ThreatGrid employs a simple rate limiting method for sample submissions by specifying the number of samples which can be submitted within some variable time period by an entire organization and/or per a license basis. Multiple rate limits can be employed to form overlapping submission limits. For example, 20 submissions per hour AND 400 per day.
Base Command
threat-grid-organization-get-rate-limit
Input
|
Argument Name
|
Description
|
Required
|
|
adminLogin
|
The admin user login name to be used for getting the rate limits
|
Required
|
Context Output
|
Path
|
Type
|
Description
|
|
ThreatGrid.User.RateLimit.Minutes
|
number
|
Array of array(s) representing submission(s) per minute(s) or the string"nil" to clear the value. Example: [[5, 1440]], which represents 5 samples per day. This field represent the minutes.
|
|
ThreatGrid.User.RateLimit.Samples
|
number
|
Array of array(s) representing submission(s) per minute(s) or the string"nil" to clear the value. Example: [[5, 1440]], which represents 5 samples per day. This field represent the number of samples allowed.
|
|
ThreatGrid.User.RateLimit.SubmissionWaitSeconds
|
number
|
The number of seconds to wait for a submission to be uploaded on the platform
|
|
ThreatGrid.User.RateLimit.SubmissionsAvailable
|
number
|
The number of submissions available for the entire organization
|
Command Example
!threat-grid-organization-get-rate-limit adminLogin="admin"
Context Example
{
"ThreatGrid": {
"User": {
"RateLimit": [
{
"SubmissionsAvailable": 47,
"SubmissionWaitSeconds": 0,
"Minutes": 1440,
"Samples": 50
}
]
}
}
}
Human Readable Output

21. Search IP addresses
Search IPs.
Base Command
threat-grid-search-ips
Input
|
Argument Name
|
Description
|
Required
|
|
network_dst
|
Destination IP
|
Optional
|
|
network_src
|
Source IP
|
Optional
|
|
artifact
|
Artifact SHA-256
|
Optional
|
|
domain
|
Domain name
|
Optional
|
|
url
|
URL
|
Optional
|
|
asn
|
IP asn
|
Optional
|
|
geo_location
|
IP geo-location information
|
Optional
|
|
cidr
|
IP/CIDR
|
Optional
|
|
ioc
|
IOC name
|
Optional
|
|
tag
|
Tag name
|
Optional
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-search-ips tag=malicious
Human Readable Output

22. Get annotation data for an analysis
Returns data about the annotations of the analysis.
Base Command
threat-grid-get-analysis-annotations
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP
|
IP address present in the annotation
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP.Asn
|
Autonomous system number of the IP
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP.City
|
IP city
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP.Country
|
IP country
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP.Org
|
IP Org
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP.Region
|
IP region
|
|
ThreatGrid.AnalysisResults.Sample.Id.Annotations.IP.Timestamp
|
IP timestamp
|
Command Example
!threat-grid-get-analysis-annotations id=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"AnalysisResults": {
"Sample": {
"Id": {
"Annotations": [
{
"IP": "192.168.1.11",
"IP.Asn": null,
"IP.Region": null,
"IP.Timestamp": 1533726370,
"IP.City": null,
"IP.Country": null,
"IP.Org": null
},
{
"IP": "255.255.255.255",
"IP.Asn": null,
"IP.Region": null,
"IP.Timestamp": 1533726370,
"IP.City": null,
"IP.Country": null,
"IP.Org": null
},
{
"IP": "0.0.0.0",
"IP.Asn": null,
"IP.Region": null,
"IP.Timestamp": 1533726370,
"IP.City": null,
"IP.Country": null,
"IP.Org": null
},
{
"IP": "192.168.1.1",
"IP.Asn": null,
"IP.Region": null,
"IP.Timestamp": 1533726370,
"IP.City": null,
"IP.Country": null,
"IP.Org": null
},
{
"IP": "192.168.1.255",
"IP.Asn": null,
"IP.Region": null,
"IP.Timestamp": 1533726370,
"IP.City": null,
"IP.Country": null,
"IP.Org": null
}
]
}
}
}
}
}
Human Readable Output
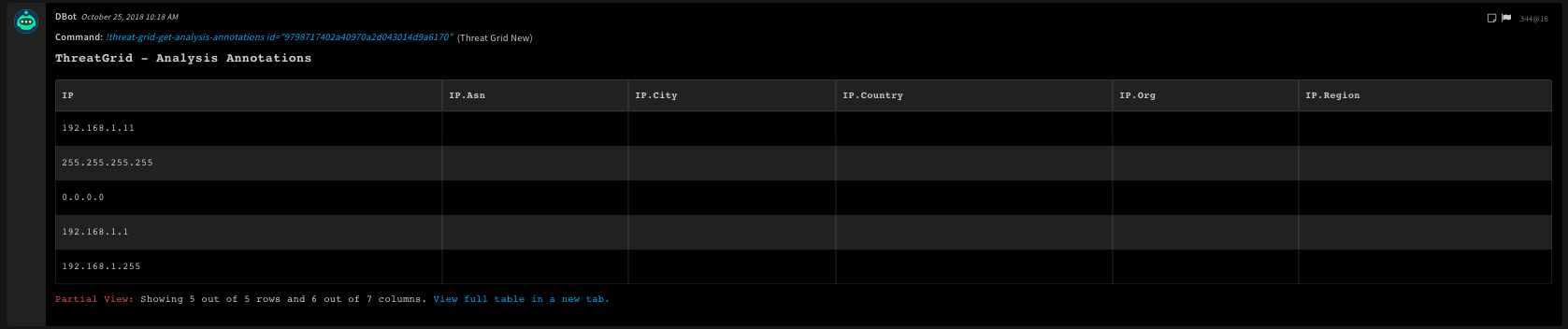
23. Search samples
Searches samples.
Base Command
threat-grid-search-samples
Input
|
Argument Name
|
Description
|
Required
|
|
ioc
|
IOC name
|
Optional
|
|
checksum
|
Checksum (SHA-256, MD5, or SHA-1)
|
Optional
|
|
checksum_sample
|
Checksum of sample
|
Optional
|
|
path
|
Path name
|
Optional
|
|
path_sample
|
Sample path name
|
Optional
|
|
path_artifact
|
Artifact name
|
Optional
|
|
path_deleted
|
search by path names that were deleted
|
Optional
|
|
url
|
search by url
|
Optional
|
|
registry_key
|
search by registry key accessed
|
Optional
|
|
domain
|
search by domain name
|
Optional
|
|
domain_dns_lookup
|
search by domain name used for DNS lookups
|
Optional
|
|
domain_http_request
|
search by domain name used in HTTP request
|
Optional
|
|
ip
|
search by ip address
|
Optional
|
|
ip_dns_lookup
|
search by IP address returned in DNS lookup
|
Optional
|
|
ip_src
|
search by network stream source IP address
|
Optional
|
|
ip_dst
|
search by network stream destination IP address
|
Optional
|
|
tag
|
search by sample tag
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Samples.Result
|
Result ID
|
|
ThreatGrid.Samples.Details
|
Detail of sample
|
Command Example
!threat-grid-search-samples checksum=d3c852ed16a7e4a4cde88266c060ee064ed047a8a43685ae52ce6c82f40e5b3f
Context Example
{
"ThreatGrid": {
"Sample": {
"Details": "/api/v2/samples/b9218ef55a1bc6d50456f32dc5e31fba",
"Result": "b9218ef55a1bc6d50456f32dc5e31fba"
}
}
}
Human Readable Output

24. Search URLs
Search URLs.
Base Command
threat-grid-search-urls
Input
|
Argument Name
|
Description
|
Required
|
|
url
|
URL pattern
|
Optional
|
|
sibling
|
URL pattern prefix
|
Optional
|
|
neighbor
|
Hostname of URL
|
Optional
|
|
sha256
|
SHA-56 of URL
|
Optional
|
|
md5
|
MD5 of URL
|
Optional
|
|
sha1
|
SHA-1 of URL
|
Optional
|
|
protocol
|
Protocol name
|
Optional
|
|
host
|
Hostname
|
Optional
|
|
port
|
Port number
|
Optional
|
|
path
|
Path name
|
Optional
|
|
query
|
Query
|
Optional
|
|
reference
|
Fragment identifier
|
Optional
|
|
ip
|
IP address of network stream
|
Optional
|
|
artifact
|
Artifact downloaded
|
Optional
|
|
tag
|
URL tag
|
Optional
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-search-urls ip=1.1.1.3
25. Get the states of samples
Returns Threat Grid samples state.
Base Command
threat-grid-get-samples-state
Input
|
Argument Name
|
Description
|
Required
|
|
ids
|
Comma-separated list of sample IDs
|
Optional
|
Context Output
|
Path
|
Description
|
|
ThreatGrid.Sample.ID
|
The sample ID, globally unique, and the canonical identifier of this sample analysis
|
|
ThreatGrid.Sample.State
|
The state of the sample, one of a stable set of strings “wait", "prep", "run", "proc", "succ", "fail”
|
Command Example
!threat-grid-get-samples-state ids=9798717402a40970a2d043014d9a6170
Context Example
{
"ThreatGrid": {
"Sample": {
"State": "succ",
"ID": "9798717402a40970a2d043014d9a6170"
}
}
}
Human Readable Output

26. Get the threat feed for artifacts
Get the threat feed for artifacts.
Base Command
threat-grid-feeds-artifacts
Input
|
Argument Name
|
Description
|
Required
|
|
sha256
|
Restrict returned records with this SHA-256
|
Optional
|
|
sha1
|
Restrict returned records with this SHA-1
|
Optional
|
|
md5
|
Restrict returned records with this MD5
|
Optional
|
|
path
|
Restrict returned records to this path or path fragment.
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before it
|
Optional
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after it
|
Optional
|
|
confidence
|
Restrict to IOCs with this confidence score or higher, defaults to 80
|
Optional
|
|
severity
|
Restrict to IOCs with this severity score or higher, defaults to 80
|
Optional
|
|
ioc
|
Restrict returned records to events of this type
|
Optional
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
|
sample
|
A comma-separated list of sample IDs. Restrict results to these samples.
|
Optional
|
Command Example
!threat-grid-feeds-artifacts after=2018-01-18T00:00:00 before=2018-01-18T00:02:07 confidence=75 severity=75
Human Readable Output
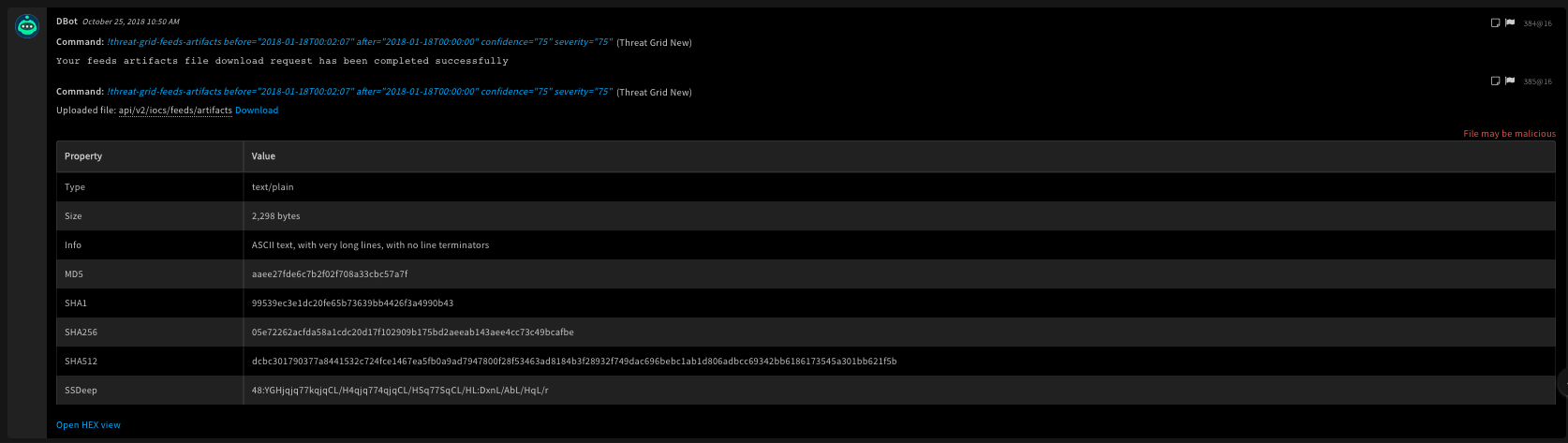
27. Get the threat feed for a domain
Get the threat feed for a domain.
Base Command
threat-grid-feeds-domain
Input
|
Argument Name
|
Description
|
Required
|
|
domain
|
Restrict returned records to this domain or hostname
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before it
|
Optional
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after it
|
Optional
|
|
confidence
|
Restrict to IOCs with this confidence score or higher, defaults to 80
|
Optional
|
|
severity
|
Restrict to IOCs with this severity score or higher, defaults to 80
|
Optional
|
|
ioc
|
Restrict returned records to events of this type
|
Optional
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
|
sample
|
A comma-separated list of sample IDs. Restrict results to these samples.
|
Optional
|
Command Example
!threat-grid-feeds-domain after=2018-01-18T00:00:00 before=2018-01-18T00:10:00 confidence=75 severity=75
Human Readable Output

28. Get the threat feed for an IP address
Returns the threat feed for an IP address.
Base Command
threat-grid-feeds-ip
Input
|
Argument Name
|
Description
|
Required
|
|
ip
|
Restrict returned records to this IP or CIDR block
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before it
|
Optional
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after it
|
Optional
|
|
confidence
|
Restrict to IOCs with this confidence score or higher, defaults to 80
|
Optional
|
|
severity
|
Restrict to IOCs with this severity score or higher, defaults to 80
|
Optional
|
|
ioc
|
Restrict returned records to events of this type
|
Optional
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
|
sample
|
A comma-separated list of sample IDs. Restrict results to these samples.
|
Optional
|
Command Example
!threat-grid-feeds-ip after=2018-01-18T00:00:00 before=2018-01-18T01:00:00 confidence=75 severity=75
Human Readable Output
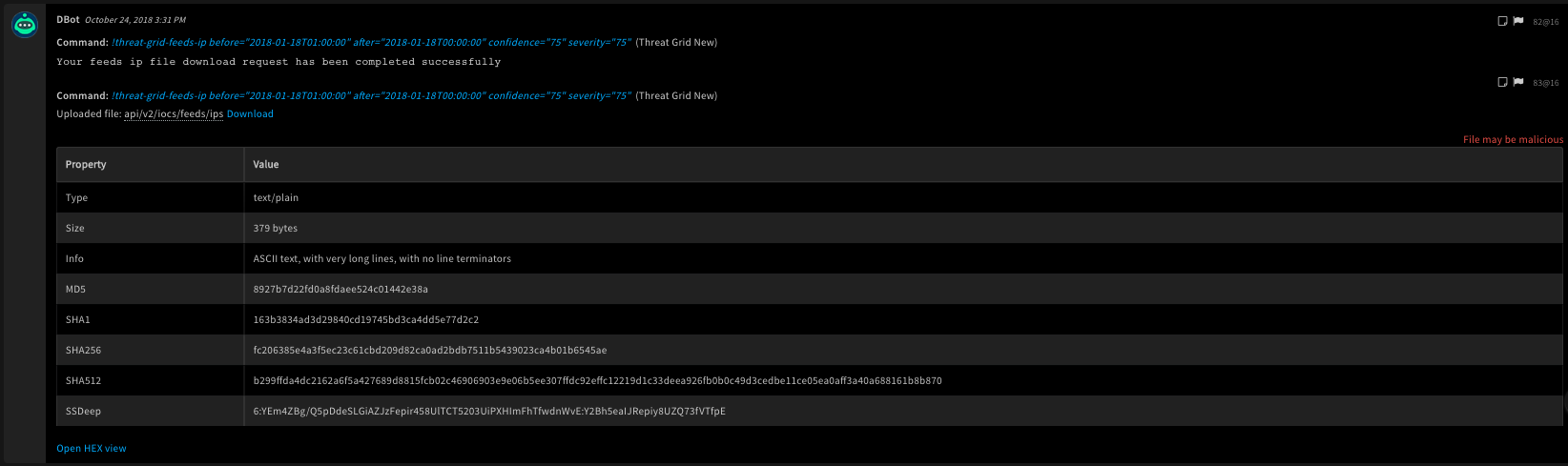
29. Get the threat feed for a network stream
Get network stream threat feed
Base Command
threat-grid-feeds-network-stream
Input
|
Argument Name
|
Description
|
Required
|
|
ip
|
Restrict returned records to this IP address
|
Optional
|
|
port
|
Restrict returned records to this port number
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before it
|
Optional
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after it
|
Optional
|
|
confidence
|
Restrict to IOCs with this confidence score or higher, defaults is 80
|
Optional
|
|
severity
|
Restrict to IOCs with this severity score or higher, defaults is 80
|
Optional
|
|
ioc
|
Restrict returned records to events of this type
|
Optional
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
|
sample
|
A comma-separated list of sample IDs. Restrict results to these samples.
|
Optional
|
Command Example
!threat-grid-feeds-network-stream after=2018-01-18T00:00:00 before=2018-01-18T00:02:10 confidence=75 severity=75
Human Readable Output

30. Get the threat feed for a path
Returns the threat feed for a path.
Base Command
threat-grid-feeds-path
Input
|
Argument Name
|
Description
|
Required
|
|
path
|
Restrict returned records to this path or path fragment
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before it
|
Optional
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after it
|
Optional
|
|
confidence
|
Restrict to IOCs with this confidence score or higher, defaults to 80
|
Optional
|
|
severity
|
Restrict to IOCs with this severity score or higher, defaults to 80
|
Optional
|
|
ioc
|
Restrict returned records to events of this type
|
Optional
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
|
sample
|
A comma-separated list of sample IDs. Restrict results to these samples.
|
Optional
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-feeds-path after=2018-01-18T00:00:00 before=2018-01-18T00:03:00 confidence=75 severity=75
Human Readable Output
31. Get the threat feed for URL
Returns the threat feed for a URL.
Base Command
threat-grid-feeds-url
Input
|
Argument Name
|
Description
|
Required
|
|
url
|
Restrict returned records to this URL or URL fragment
|
Optional
|
|
before
|
A date/time (ISO 8601), restricting results to samples submitted before it
|
Optional
|
|
after
|
A date/time (ISO 8601), restricting results to samples submitted after it
|
Optional
|
|
confidence
|
Restrict to IOCs with this confidence score or higher, default is 80
|
Optional
|
|
severity
|
Restrict to IOCs with this severity score or higher, default is 80
|
Optional
|
|
ioc
|
Restrict returned records to events of this type
|
Optional
|
|
org-only
|
If “true”, will only match against samples submitted by your organization
|
Optional
|
|
user-only
|
If “true”, will only match against samples you submitted
|
Optional
|
|
sample
|
A comma-separated list of sample IDs. Restrict results to these samples.
|
Optional
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-feeds-url after=2018-01-18T00:00:00 before=2018-01-18T00:05:00 confidence=75 severity=75
Human Readable Output

32. Get the artifact for a sample ID by artifact ID
Returns the sample ID artifact with artifact id
Base Command
threat-grid-get-analysis-artifact
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
|
aid
|
The artifact ID requested
|
Required
|
Command Example
!threat-grid-get-analysis-artifact id=a6cc7ae4e3318e98d94e8a053dd72c47 aid=1
Human Readable Output
33. Get artifacts for a sample ID
Returns the sample id artifacts
Base Command
threat-grid-get-analysis-artifacts
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-get-analysis-artifacts id=a6cc7ae4e3318e98d94e8a053dd72c47
Human Readable Output

34. Get analysis data for an IOC
Returns data for the specified IOC.
Base Command
threat-grid-get-analysis-ioc
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
|
ioc
|
The requested IOC
|
Required
|
Command Example
!threat-grid-get-analysis-ioc id=8ee72188b95b7d8f4e1a6c4842e98566 ioc=network-communications-http-get-url
Human Readable Output

35. Get metadata for an analysis
Returns metadata about the analysis.
Base Command
threat-grid-get-analysis-metadata
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Command Example
!threat-grid-get-analysis-metadata id=58e5e66b31484a8529b80a18a33e0814
Human Readable Output
36. Get data for a network stream
Returns data regarding a specific network stream
Base Command
threat-grid-get-analysis-network-stream
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
|
nsid
|
The network stream ID
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-get-analysis-network-stream id=a6cc7ae4e3318e98d94e8a053dd72c47 nsid=1
Human Readable Output

37. Get the analysis for a network stream
Returns the network stream analysis.
Base Command
threat-grid-get-analysis-network-streams
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-get-analysis-network-streams id=a6cc7ae4e3318e98d94e8a053dd72c47
Human Readable Output

38. Get data for a process ID in an analysis
Returns data regarding the specific process ID in the analysis.
Base Command
threat-grid-get-analysis-process
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
|
pid
|
The requested process ID
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-get-analysis-process id=9798717402a40970a2d043014d9a6170 pid=4
Human Readable Output

39. Get data for an analysis process
Returns data regarding the analysis processes.
Base Command
threat-grid-get-analysis-processes
Input
|
Argument Name
|
Description
|
Required
|
|
id
|
The sample ID
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-get-analysis-processes id=9798717402a40970a2d043014d9a6170
Human Readable Output

40. Submit URLs for analysis
Submit the URL for Threat analysis processes.
Base Command
threat-grid-submit-urls
Input
|
Argument Name
|
Description
|
Required
|
|
url
|
The URL to submit to ThreatGrid
|
Required
|
Context Output
There is no context output for this command.
Command Example
threat-grid-submit-urls url="www.example.com"
41. Advanced search for URLs/Samples already submitted for analysis
Perform advanced search on ThreatGrid
Base Command
threat-grid-advanced-search
Input
|
Argument Name
|
Description
|
Required
|
|
query
|
ThreatGrid search query to run
|
Required
|
Context Output
There is no context output for this command.
Command Example
!threat-grid-advanced-search query="{
\"query\": \"query get_sample($q_json:
String) {sample(, q_json: $q_json,limit: 3) {submitted_at id submitted_file_type status threat_score state login url}}\",\"variables\": {\"q_json\": \"{\\\"op\\\": \\\"and\\\",\\\"clauses\\\": [{\\\"op\\\": \\\"attr\\\",\\\"attr\\\": \\\"submitted_file_name\\\",\\\"comp_op\\\": \\\"eq\\\",\\\"value\\\": \\\"www.example.com_.url\\\"}]}\"}}"




































