ReversingLabs A1000 (Deprecated)
This Integration is part of the ReversingLabs A1000 Pack.#
Deprecated
Use the ReversingLabs A1000 v2 integration instead.
Overview
Use the A1000 Malware Analysis Platform to support advanced hunting and investigations through high-speed automated static analysis. A1000 Malware Analysis Platform is integrated with file reputation services to provide in-depth rich context and threat classification on over 6B files and across all file types.
This integration was integrated and tested with ReversingLabs A1000 Malware Analysis Platform™, 3.7.1.4.
Use Cases
- Supports automated analysis processes (Static Analysis) that includes unpacking and identifying the families of archives, installers, packers and compressors.
- Extracts over 3,000 PTIs from extracted files for PE/Windows, ELF/Linux, Mac OS, iOS, Android, firmware, and documents.
- Calculates file threat level using extracted information.
Helps in regulating the investigation process by uploading and downloading samples to A1000 cloud platform at any point in time. (File reputation data can also be retrieved from an A1000 appliance.)
Prerequisites
You need to obtain the following ReversingLabs A1000 platform information.
- Base URL of the A1000 box (https://a1000.reversinglabs.com)
- Authentication Token
Get Your ReversingLabs A1000 Authentication Token
- Log in to the ReversingLabs A1000 platform.
- Navigate to Administration and click the Tokens icon.
- On the Authentication Tokens page, click the red plus button to create a new token key.
-
Select the necessary user, and click the
Save
button.
The new key is listed on the token table. - Copy the key (authentication token), which you will paste when you configure the integration on Cortex XSOAR.
Configure ReversingLabs A1000 Cortex XSOAR
- Navigate to Settings > Integrations > Servers & Services .
- Search for ReversingLabs A1000.
-
Click
Add instance
to create and configure a new integration instance.
- Name : a textual name for the integration instance.
- Base URL of the A1000 box : https://a1000.reversinglabs.com
- Authentication Token : paste the token that you copied.
- Click Test to validate the URLs and connection.
Commands
You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook. After you successfully execute a command, a DBot message appears in the War Room with the command details.
- Upload a sample to A1000 for analysis: reversinglabs-upload
- Re-analyze sample set: reversinglabs-analyze
- Download a sample to the investigation: reversinglabs-download
- Download samples obtained through the unpacking process: reversinglabs-download-unpacked
- List extracted files from a sample: reversinglabs-extracted-files
- Delete an uploaded sample: reversinglabs-delete
- Retrieve file reputation data from an A1000 appliance: file
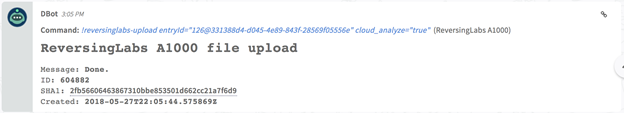
Upload a sample to A1000 for analysis : reversinglabs-upload
Upload a sample to A1000 for analysis.
Command Example
!reversinglabs-upload entryId="
126@331388d4-d045-4e89-843f-28569f05556e
" cloud_analyze="
true
"
Input
|
Parameter |
Description |
|
entryId |
Entry ID of the file to be uploaded. (Once you upload a file on Cortex XSOAR’s platform, click on the link(chain) icon to get the entry ID of that file) |
|
comment |
A comment for the file to be uploaded. |
|
tags |
A comma separated list of tags for the file. |
|
cloud_analyze |
Specifies if the sample is sent to TiCloud for scanning. By default the value is true .
|
Human Readable Output
Raw Output
{
"code": 201,
"message": "Done.",
"detail": {
"id": 604883,
"sha1": "2fb56606463867310bbe853501d662cc21a7f6d9",
"user": 585,
"created": "2018-05-27T22:32:06.830474Z",
"filename": "2018-05-24-Trickbot-malspam-1140-UTC.eml",
"href": "/?q=2fb56606463867310bbe853501d662cc21a7f6d9"
}
}
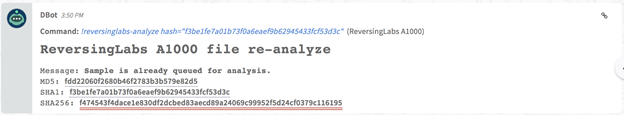
Reanalyze sample set: reversinglabs-analyze
Schedule a set of samples that were previously updated to the A1000 appliance to be reanalyzed.
Command Example
!reversinglabs-analyze hash="
2fb56606463867310bbe853501d662cc21a7f6d9
"
Input
|
Parameter |
Description |
|
hash |
The hash of a previously uploaded sample. Hexadecimal representation of SHA-1, SHA-256, SHA-512, or MD5 digest. |
Human Readable Output
Raw Output
{
"code": 200,
"message": "Sample is already queued for analysis.",
"detail": {
"sha1": "f3be1fe7a01b73f0a6eaef9b62945433fcf53d3c",
"Sha256": "f474543f4dace1e830df2dcbed83aecd89a24069c99952f5d24cf0379c116195",
"md5": "fdd22060f2680b46f2783b3b579e82d5"
}
}
Download a sample to the investigation: reversinglabs-download
Download a sample that resides on A1000 to the investigation.
Command Example
!reversinglabs-download hash="
fdd22060f2680b46f2783b3b579e82d5
"
Input
|
Parameter |
Description |
|
hash |
The hash of a sample that resides on A1000. Hexadecimal representation of SHA-1, SHA-256, SHA-512, or MD5 digest. |
Human Readable Output
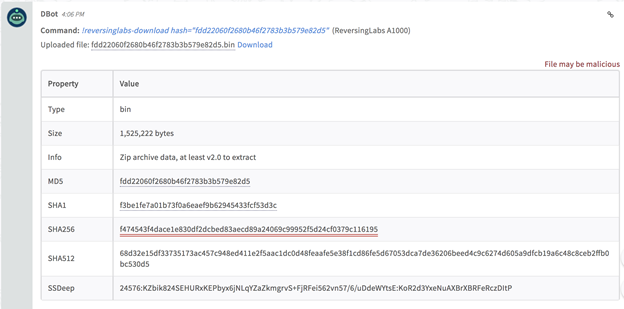
Raw Output
There is no raw output for this command.
When the command runs successfully, you get a downloadable file.
When the command fails, you receive a notification with one of the following error codes.
- 404 - Sample not found.
- 401 - Unable to retrieve sample content.
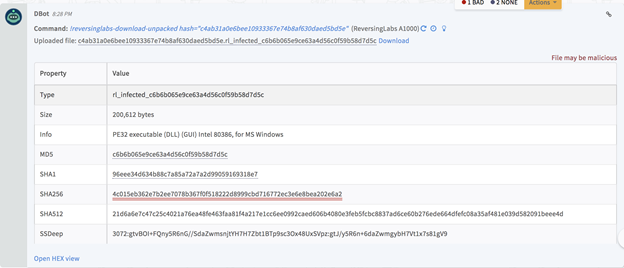
Download samples obtained through the unpacking process : reversinglabs-download-unpacked
Download samples obtained through the unpacking process.
Command Example
!reversinglabs-download-unpacked hash="
6bb767e20c25e4d37e73fc0733c7ef2fce4ac8c6
"
Input
|
Parameter |
Description |
|
hash |
The hash of a sample that resides on A1000. Hexadecimal representation of SHA-1, SHA-256, SHA-512, or MD5 digest |
Human Readable Output
Raw Output
There is no raw output for this command.
When the command runs successfully, you get a downloadable file.
When the command fails, you are receive a notification with one of the following error codes.
- 404 - Sample not found.
- 401 - Unable to retrieve sample content.
List extracted files from a sample : reversinglabs-extracted-files
List extracted files from a sample
Command Example
!reversinglabs-extracted-files hash="
f3be1fe7a01b73f0a6eaef9b62945433fcf53d3c
"
Input
|
Parameter |
Description |
|
hash |
The hash of an already uploaded sample. Hexadecimal representation of SHA-1, SHA-256, SHA-512, or MD5 digest |
Human Readable Output
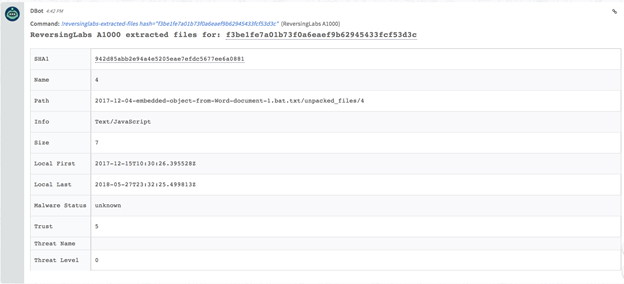
Raw Output
{
"count": 5,
"next": null,
"previous": null,
"results": [
{
"id": 197,
"parent_relationship": null,
"sample": {
"id": 192,
"sha1": "e906fa3d51e86a61741b3499145a114e9bfb7c56",
"type_display": "PE/Exe",
"category": "application",
"file_type": "PE",
"file_subtype": "Exe",
"identification_name": "",
"identification_version": "",
"file_size": 267278,
"extracted_file_count": 2,
"local_first_seen": "2016-05-05T09:57:50.910412Z",
"local_last_seen": "2016-05-05T13:43:21.282072Z",
"threat_status": "malicious",
"trust_factor": 5,
"threat_level": 5,
"threat_name": "Win32.Trojan.Bitman"
},
"filename": "DeVuongHoi.exe",
"path": "DeVuongHoi.exe"
},
{
"id": 198,
"parent_relationship": null,
"sample": {
"id": 198,
"sha1": "e654d39cd13414b5151e8cf0d8f5b166dddd45cb",
"type_display": "PE/Exe",
"category": "application",
"file_type": "PE",
"file_subtype": "Exe",
"identification_name": "",
"identification_version": "",
"file_size": 290816,
ReversingLabs
123
"extracted_file_count": 1,
"local_first_seen": "2016-05-05T09:58:27.096525Z",
"local_last_seen": "2016-05-05T09:58:27.096525Z",
"threat_status": "malicious",
"trust_factor": 5,
"threat_level": 5,
"threat_name": "Win32.Malware.YARA"
},
"filename": "DieGroupv8.exe",
"path": "DieGroupv8.exe"
},
...
Delete an uploaded sample : reversinglabs-delete
Delete an uploaded sample for the specified hash value that resides A1000. All related data, including extracted samples and metadata, will be deleted.
Command Example
!reversinglabs-delete hash=" 942d85abb2e94a4e5205eae7efdc5677ee6a0881 "
Input
|
Parameter |
Description |
|
hash |
The hash of a sample that resides on A1000. Hexadecimal representation of SHA-1, SHA-256, SHA-512, or MD5 digest |
Human Readable Output
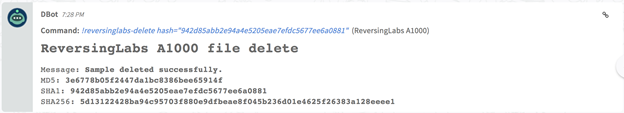
Raw Output
{
"code": 200,
"message": "Sample deleted successfully.",
"detail": {
"sha1": "f3be1fe7a01b73f0a6eaef9b62945433fcf53d3c",
"Sha256": "f474543f4dace1e830df2dcbed83aecd89a24069c99952f5d24cf0379c116195",
"Sha512": "68d32e15df33735173ac457c948ed411e2f5aac1dc0d48feaafe5e38f1cd86fe5d67053dca7de36206beed4c9c6274d605a9dfcb19a6c48c8ceb2ffb0bc530d5"
"md5": "fdd22060f2680b46f2783b3b579e82d5"
}
}
Retrieve file reputation data from an A1000 appliance : file
Retrieve file reputation data from an A1000 appliance.
Command Example
!file file="
8437682e44a764d0c0f610f6cb262a98
"
Input
|
Parameter |
Description |
|
file |
The hash that you want to retrieve reputation data for. Hexadecimal representation of SHA-1, SHA-256, SHA-512, or MD5 digest. |
Human Readable Output
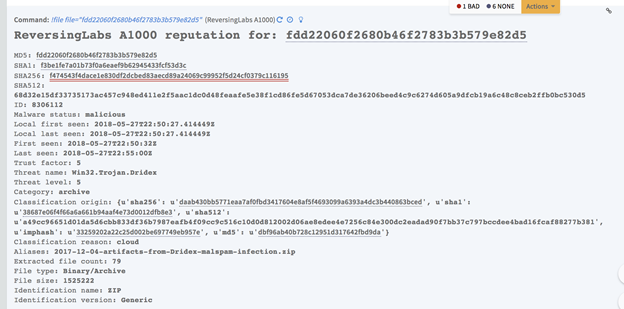
Context Output
|
Parameter |
Description |
|
File.MD5 |
Bad hash detected. |
|
File.SHA1 |
Bad hash SHA-1. |
|
File.Malicious.Vendor |
For malicious files, the vendor that made the decision. |
|
File.Malicious.Detections |
For malicious files, the total number of detections. |
|
File.Malicious.TotalEngines |
For malicious files, the total number of engines. |
|
DBotScore.Indicator |
The indicator that is being tested. |
|
DBotScore.Type |
Indicator type. |
|
DBotScore.Vendor |
Vendor used to calculate the score. |
|
DBotScore.Score |
The actual score |
Raw Output
"results": [
{
"category": "archive",
"aliases": {
"0": "2017-12-04-artifacts-from-Dridex-malspam-infection.zip"
},
"classification_origin":{
"imphash": "33259202a22c25d002be697749eb957e",
"md5": "dbf96ab40b728c12951d317642fbd9da",
"sha1": "38687e06f4f66a6a661b94aaf4e73d0012dfb8e3",
"sha256": "daab430bb5771eaa7af0fbd3417604e8af5f4693099a6393a4dc3b440863bced",
"sha512": "a49cc96651d01da5d6cbb833df36b7987eafb4f09cc9c516c10d0d812002d06ae8edee4e7256c84e300dc2eadad90f7bb37c797bccdee4bad16fcaf88277b381"
}
"classification_reason": "cloud",
"extracted_file_count": 79,
"file_size": 1525222,
"file_subtype": "Archive",
"file_type": "Binary",
"identification_name": "ZIP",
"identification_version": "Generic",
"local_first_seen": "2018-05-27T22:50:27.414449Z",
"local_last_seen": "2018-05-27T22:50:27.414449Z",
"md5": "fdd22060f2680b46f2783b3b579e82d5",
"sha1": "f3be1fe7a01b73f0a6eaef9b62945433fcf53d3c",
"sha256": "f474543f4dace1e830df2dcbed83aecd89a24069c99952f5d24cf0379c116195",
"sha512": "68d32e15df33735173ac457c948ed411e2f5aac1dc0d48feaafe5e38f1cd86fe5d67053dca7de36206beed4c9c6274d605a9dcb19a6c48c8ceb2ffb0bc530d5",
"summary":{
"id": 8306112,
"indicators": []
}
"sha1": "f3be1fe7a01b73f0a6eaef9b62945433fcf53d3c",
"threat_level": 5,
"threat_name": Win32.Trojan.Dridex,
"threat_status": malicious,
"ticloud": {
"first_seen": "2018-05-27T22:50:32Z",
"last_seen": "2018-05-27T22:55:00Z",
"threat_level": 0,
"threat_name": null,
"threat_status": "known",
"trust_factor": 5,
"Trust_factor" 5
}
}